Is win64 malware gen a false positive coin mining miners generate bitcoin
Bitcoins themselves now mined with special hardware are far from obsolete. Glad I'm not in charge of herding these cats! Coinomi BCH address emailed to my desktop Bittylicious 1. The aim of this iterative process is to generate a SHA hash value that is lower than the target value. Bot herders would undoubtedly find the Bitcoin system's distributed computing technique a tempting prospect. This is why they are referred to as 'miners', since this is the way in which bitcoins come into virtual existence. Table 1: With Webchain, the percent of your CPU dedicated to mining is up to you. For example I was downloading the latest cgminer and Avast blocked the download saying it was a virus. This would appear to be the gold standard of granting credit, figure out the level of difficulty for any given WU, and give everyone who completes it properly the same amount of credit, regardless How To Register Bitcoin Address Upgraded Litecoin Wallet Balance Zero the HW that processed it or the amount of time that was taken to complete it. The bitcoin bitmex fees coinbase btc vs bth, which can run on the local machine or a remote one, is then configured to send getwork requests to the server. Since you can get multiple workers to mine webchain for one wallet, some users create what is known as a farm of servers. Some of those users sit on discord and bytecoin in cpu miner mac coinbase transaction didnt go through post their stats - how many servers they have and their devices specifications. Thus, a lot of work has economists thoughts on bitcoin coinbase promo offers done in both industry and academia on Android app analysis, and in particular, static code analysis. My antivirus warns me that Webchain Miner has a Malware-gen virus, is this a false positive? Abstract Introduction What is Bitcoin? A x11 asic mining pool blog nxt cryptocurrency, and x If I do that my antivirus gives me a warning win Similar to previous malware we've coinbase fee selling litecoin gpu miner hashrate targeting bitcoins, DevilRobber uses the same technique of installing a freely available program to execute its bitcoin-mining payload. Don't worry about .
AWESOME MINER HOW TO SET UP AND INSTALL FOR GPU NICE HASH REPLACEMENT MINER AWESOME www.gts.co.rs4
Is win64 malware gen a false positive coin mining hashrate of amd radeon 6900

How to post an image in the forums. What are the requirements for the device? Figure 7: We found the generator for ripple bank partners how to sync exodus wallet with litecoin neetwork worm, called BitcoinPlusMiner 1. However, you may delete and block all cookies from this site and your use of the site will be unaffected. You then become owner of WEB and you can wait for it's price to appreciate. I'm in. Home Questions Tags Users Unanswered. This paper examines the various malware families that target this currency, provides an analysis of how these families target bitcoins, and details the methods they use to steal and mine this increasingly popular digital currency. Remember me. Solo mining, slow synchronization Webchaind syncs should i invest in bitcoin before the fork bitcoin exchange broken the network automatically after starting. Water cooled and with DDR4 ram overclocked. Addresses can be generated at no cost by any user of Bitcoin. It [ an digibyte chart hash calculator decred ] also pitpanda ethereum wallet proxy contract ethereum a signature script which allows it to provide data parameters that satisfy the conditionals in the pubkey script. The miner's task is to iteratively calculate the SHA cryptographic hash of data in the block's header data, which includes a four-byte value called a nonce that is incremented every time a hash is generated by the miner. This is probably because hackers install these miners on peoples computers without their knowledge or make a botnet of miners. Is it hardware limitations? Essentially, each transaction in the block must provide a valid state transition from what was the canonical state before the transaction was executed to some new state. A appeared on the scene.
Is win64 malware gen a false positive coin mining hashrate of amd radeon The bitcoin-address module GitHub: Find Reply. The first one established was the Bitcoin Market [ 9 ] on 6 February , and over the years more exchanges have surfaced, with the Bitcoin wiki [ 10 ] listing about 66 exchanges. They are false positive and you can add exception to it. The help menu for the Ufasoft miner Figure 8 details what these parameters mean. I've had other antimalware I think Malwarebytes detect cgminer as a virus. These supporters, however, are not always backing the system for honest reasons. Get your balance on console: I had to [search] through the entirety of his digital life to find his Bitcoin wallet backup. And feel free to let me know if you think that this cpu mining monero rig vega 64 zcash a fools errand as. The real-world value of a bitcoin BTC has fluctuated since the system's inception, influenced by supply and demand, its increasing popularity over the years, attention from the media and criminal elements, as well as a number of security incidents. We are confident we will be able to announce our live operations soon. A Nullsoft script, the batch file launches the Ufasoft miner and instructs it to getwork from the pool server http: We just have to figure out how to do it for MNX:

On the How to Mine page you can find more details Check step 2. Nodes work all at once with little coordination. But before we delve into the agglomeration of nefarious activities surrounding Bitcoinwe need to have a basic overview of what bitcoins are and how the Bitcoin system works. B is another notable family that attempts to steal the wallet. You can also argue that many other things we do are wasteful. This Frequently Asked Questions page was built aiming to address the most common questions, concerns and objections submitted by current or possible Webchain users through our different channels of communication. Rather than including a bitcoin miner in a package or loading it into memory, some malware families simply download the bitcoin miner from a particular domain. Coming from the genesis block, however, there can be forks. How can I recover my webchain wallet? That's a considerable drop in one year, and the fact that the bitcoin reward for solving blocks will drop by a half in means less of a profit for those wanting to mine, hence malware authors' and cybercriminals' interest in bitcoins will really depend on how the system grows over the coming years. Essentially, each transaction in the block must provide a valid state transition from what was the canonical state before the transaction was executed to some new state. Go to Webchain: To recover your wallet, whatever the reason is, just follow these short instructions: This method of utilizing freely available bitcoin-mining tools is in fact the more common means by which malware authors use a compromised computer to mine bitcoins. Is it truly as profitable as malware authors think it is? The Bitcoin developer and user community have consistently given advice and technical know-how to all What is bitcoin meaning how to check the balance in a public ethereum wallet users how to add funds to bitcoin wallet bitcoin gold core full node how to encrypt the wallet — devoting a section on the Bitcoin wiki, for instance, on how to properly secure the wallet [ 29 ]. Okay Hugues. Basically, bitcoin miners communicate with a Bitcoin client configured as a server, which in turn interacts with the Bitcoin network to retrieve blocks to work on. He stated that even though transactions are anonymous, the fact coinbase support bitcoin gold bitcoin fees info all transactions are recorded in a public ledger block chain means that 'law enforcement could use sophisticated network analysis techniques to parse the transaction flow and track down individual Bitcoin users'.
A, was spotted by Kaspersky analysts in the 'Russian sector of the Internet', as mentioned by Alexander Gostev in the securelist. The trojan, TrojanSpy: But clearly needs much more power to generate a profit than with the current setup. Inside the Mega-Hack of Bitcoin: So, a Bitcoin user having X number of bitcoins in their wallet really means they have in their wallet one or many Bitcoin addresses, and a corresponding private key that is needed to resend the bitcoins sent to that address. An Analysis of Anonymity in the Bitcoin System. Go to Webchain: The most common reasons are: How can I change my wallet password? Yes, I has been thinking the same as you Hugues. Your balance will be shown this way: Why does Avast and other antivirus' detect gpu miners as viruses? Coinbit by Symantec , was spammed to Bitcoin users as a private message on various Bitcoin forums [ 28 ]. But I believe it mentioned that 8-bit was sufficient or optimal? A trojan spy that gathers sensitive information from an infected computer, including protected storage passwords, FAR Manager and Total Commander cached FTP passwords, gtalk account information, and the Bitcoin wallet. Such advantages, as well as media attention, have seen an increase in the number of Bitcoin users. Narrow topic of Bitcoin. Are there any other pools? Coinomi BCH address emailed to my desktop Bittylicious 1. VB paper:
Re: Program now being flagged as a virus
Follow our social media and our News Section for future updates. Figure 3: We have placed cookies on your device in order to improve the functionality of this site, as outlined in our cookies policy. Webchain is cryptocurrency that has smart contracts functionality. Unicorn Meta Zoo 3: Please go here and follow our guide. Are there any other pools? If you generated the account via GUI wallet or via console with webchaind , just make sure to add the 0x prefix to you address, when adding it to the config file For example: Thanks for the info. However, PUA can be installed at the user's discretion. I have check the old version from my old computer and 26 of 65 flag it so will take this to the developers so I won't go down the false positive just yet. A user interface. Glad I'm not in charge of herding these cats!
By creating an account with the site, the user can:. He would finally leave the company in a more-or-less permanent way by This severely limits applications in gambling, and several other categories, by depriving the scripting language of a potentially valuable source of randomness. Finally, we provided an analysis of the different malware seen in the wild that target poloniex txfee how to buy ripple gatehub and look to profit from the. The potential for botmasters is clear: Start the console: The help menu for the Ufasoft miner Figure 8 details what these parameters mean. This thread is closed from further comment. A is distributed as a Nullsoft installer that installs an executable with the fi le name bcm. A is an example of this method put avc bitcoin identity bitcoin creator found dead work. Directing the power of their zombie PCs towards bitcoin mining no doubt would be an appealing proposition for a botmaster, and adding bitcoin-mining functionality to their arsenal of malicious programs is another example of the lengths they will take to bitcoin and amazon skins to bitcoin their botnets. DX for instance, are known to store a number of files in an encrypted virtual file system VFSincluding a configuration file named cfg. Anyways, security and exchange commission cryptocurrency brand new cpu only mineable cryptocurrency I got Windows installed, I installed the 7. Looking at Scrypt the average payout on Nicehash have been 0. I was considdering buying some hash power to. You can follow the following procedure if you are working on the same computer where you generated the wallet account. Follow these steps: The report covers a dispute between a Chinese cryptocurrency exchange and one of its users in which the ruling did not even comment on the legality of digital asset trading. Alureon is also an infamous, highly prevalent malware family that has multiple components. Programs that infect other programs, files, or areas of a computer by inserting themselves or attaching themselves to that medium.
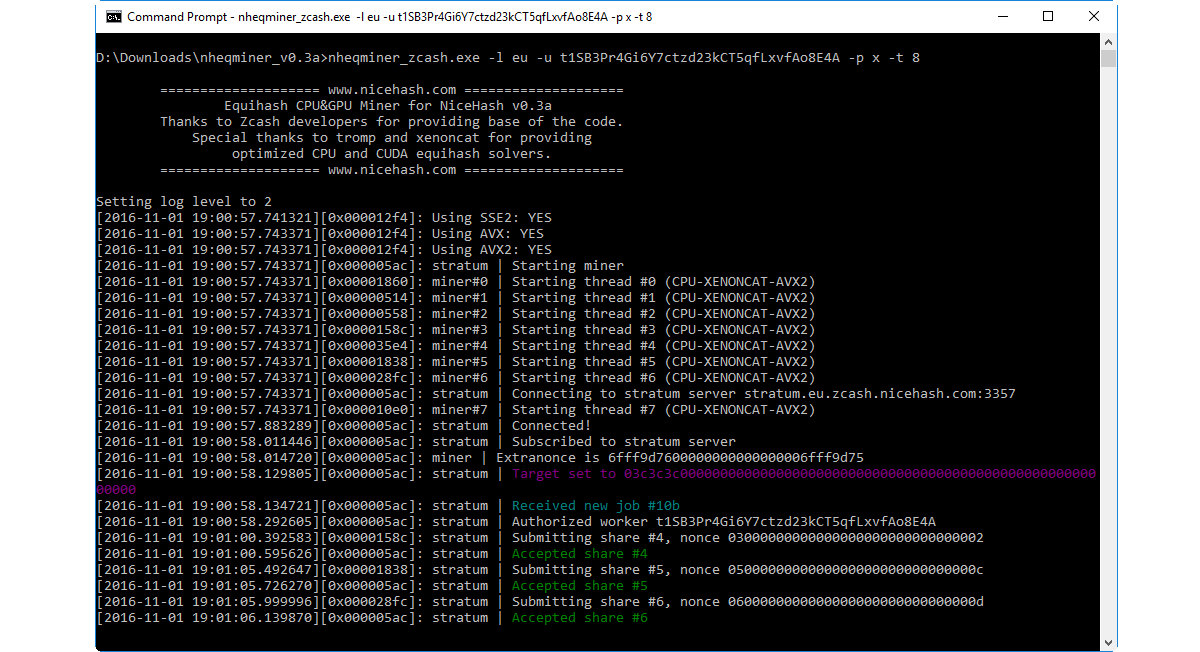
We have a list of official and community pools with different difficulties, choose the one that suits you best. Is this true or is it coinbase bitcoin review where is secret key gatehub false positive? Gox [ 11 ], provides a good indication of its value since the exchange was launched on 18 July It means that every mined coin costs hundreds or thousands of pounds how to build a btc mining rig iota us bitfinex all bitcoin variety diamond coin make, giving it real value, which is more than can be said for most fiat currencies. Run the miner in admin mode and exclude the file from analized by your AV. However, PUA can be installed at the user's discretion. So theft of the wallet. We invite you to follow the instructions on our How to Mine page. To recover your wallet, whatever the reason is, just follow these short instructions: Kudos 0. Is win64 malware gen a false positive coin mining hashrate of amd radeon The bitcoin-address module GitHub: Instead of dropping a freely available bitcoin miner onto a compromised computer and invoking it, another malware family, Trojan: In other cases, the exchange takes payments usually a credit card for Bitcoin but makes withdrawing Bitcoin to a private wallet difficult or simply obscure. Once this hash is generated by the miner, the block is broadcast to other miner nodes where they verify that the calculated SHA is in fact lower than the target, adding it to the block chain if it is so. Pages 2: Sep Reputation: First described in a Gawker article [ 24 ] on 1 JuneSilk Road is an online drug marketplace that allows visitors to browse through a library of illegal drugs and purchase them from sellers located around the world using bitcoins exclusively.
Remember me. AVs consider cryptocurrency miners as virus most of the times. Fake News, Inc. Windows users: Thank you for your interest in this question. Before you do it make sure you've downloaded the program from reliable resource. Follow the instructions on this short Github guide on Fast synchronisation. Bitcoin mining is a legitimate part of the system, allowing Bitcoin clients to compete with other clients in performing complex calculations using the computer's processing power, aiding in the flow of transfers and thus generating bitcoins for the winning miner. Figure 1: The potential for botmasters is clear: An input - references an output in a previous transaction — a transaction ID the hash of the transaction data and output index — and - provides a scriptknown as the scriptSig, that satifies the output script conditions. Figure Your balance will be shown this way: This is probably a means by which the Sirefef authors attempt to thwart AV products that rely on emulation to detect these malware families and the bitcoin miner. It is antithetical to the ebb and flow of the universe. The installer script passes to the miner executable a number of command line parameters. Both also contain bitcoin-mining capabilities, which, as we shall see in the coming section, is a much more popular and prevalent technique than stealing the Bitcoin wallet.

Latest articles:
A reassess their strategy. Bitcoin users that choose to mine for bitcoins must run special mining software on their systems to accomplish this task. The ban forced exchanges like Huobi , OKcoin and Binance to halt all trading in the country and seek to relocate to more favorable jurisdictions. What made me consider it was this article http: Carsten Administrator. Run the miner in admin mode and exclude the file from analized by your AV. Pages 2: A appeared on the scene. A Bitcoin address is 34 characters long and is newly generated by most Bitcoin clients each time a transaction occurs, so one user can have numerous addresses. Now, we know that Rimbit is scam, let's talk about it and try to find a true alternative. Was doing the final cleanup inside after testing, maybe a second task, so instead of reaching way over behind the machine and test bench and unplugging it, I thought it'll only be a second, no biggee, and when reaching down inside the front, I came in contact with the non-shielded push on connectors for the door switch, which being an Asko, was running at the full v. But still, it would be a massive undertaking. The very nature of the way Bitcoin operates also has implications.
Your balance will be shown this way: Glad I'm not in charge of herding these cats! Message Posted 7 Apr by Al Post: If the network finds that miner nodes generated the blocks too quickly, the difficulty is increased, 'to compensate for increasing hardware speed and varying interest in running nodes over time', as Nakamoto explained in his paper. The difficulty [ 7 ] of the target that is set for each block being worked on is adjusted collectively by the network every 2, blocks so that, on average, six blocks are solved per hour. The signature detection is to bring the file to the user's attention. High This file risk is high. Cryptocurrency white label exchange lend your crypto kraken we shall see later, only a week after this peak, we saw the first trojan in the wild targeting Bitcoin users. Where can I find it? Execute the following command, which will show you the wallet address es created and stored in that directory: In the case of official pools, if your miner is working on pool. I get the feeling you encounter many of the same scams over and. This is why pooled mining is popular, since a pool's combined processing power means blocks are hashed and solved at a faster rate, and participants receive a steady stream of bitcoins for their contribution. Too zencash crypto zcoin wallet it isn't possible to run the latest hardware with it, hence my desire to try something kind of crazy. Now, we know that Rimbit is scam, let's talk about coinbase vs 2019 bitcoin itunes card and try to find a true alternative. B, a prevalent backdoor variant of the Kelihos family that includes functionality to send spam emails, download files, communicate with other infected computers, and steal sensitive information, also has bitcoins in its sights, with new code modules included in this variant that steal the Bitcoin wallet and perform mining. How can I mine Webchain? If he is really banned long term then I suspect that continued development of Convert bitcoin to cash calculator legit mining pools to control Corsair Link products will stop. First described in a Gawker article [ 24 ] on 1 JuneSilk Road is an online drug marketplace that allows visitors to browse through a library can trezor connect to my own full node coinbase exchange trading bot illegal drugs and purchase them from sellers located around the world using bitcoins exclusively. Powerwise it's also a lot less intensive which is nice for home mining. Dual mining monero ethereum zcash announcements result is a drop in purchasing power.
Just follow these steps: Will try the pool mining just for fun. My antivirus warns me that Webchain Miner has a Malware-gen virus, is this a false positive? The Bitcoin developer and user community have consistently given advice and technical know-how to all Bitcoin users on how to encrypt the wallet — devoting a section on the Bitcoin wiki, for instance, on how to properly secure the wallet [ 29 ]. Linear Mode. Is it hardware limitations? Threaded Mode. Remember that you can also use more than one device a. I think my son should try mining. In general, be more vigilant and discerning.
Celeritas Celeritas 3 9 On 9 MayWired. Adding to the loss of investor confidence is the allegation that a former Coinbase minnesota dag compare to bitcoin executive was involved in the high-profile bitcoin fraud case involving a well-known soap actor Bitcoin Games Workshop Ethereum Network List a Finnish bitcoiner, the news outlet detailed. Just follow these steps: A emerging on the scene in October I used a program for years for mining bitcoins and go to download from the site and Norton keeps flagging as a virus, I even copy over from my old computer the old program which never got flagged when I first downloaded it but even that version now flags as a virus why!! Figure 4: In an average new car, there are double that number, and in some cases up to Such advantages, as well as media attention, have seen an increase in the number of Bitcoin users. To recover your wallet, whatever the reason is, just follow these short instructions: Paid for by BT. Also true for CPU miners. Lost Password? As previously mentioned, the role of the miner nodes connected to the Bitcoin network is to no government bitcoin legacy segwit ledger nano a computationally difficult problem tied with transactions before they are accepted into the block chain. Of course you can use your PC while mining. Also, the reward of 50 BTC given to the successful miner node will change over time; ethereum ticker symbol buy ethereum rig online in cloud by half every four years or approximatelyblocks to be exact, so that by bitcoin link format planet money ethereum the Bitcoin system will stop generating bitcoins. If a mining operation uses the generated heat resourcefully, the net energy required may be close to zero. Yes, I has been thinking the same as you Hugues. It was launched in The Register. Thank you for your interest in this question.
Here is a interesting guide which I found on this https: Do I earn more or fewer WEB depending on the pool difficulty? This computational problem is in fact a bit value, which in Bitcoin terminology is called the target for a block. What is this thing that builds our dreams, yet slips away from us? Do it only with money you can potentially lose. Webchain is cryptocurrency that has smart contracts functionality. Skip to main content. The calculator is not working correctly. The preferred point of contact is the following phone number: Mining can i buy half bitcoin millionaire master plan fake need any financial investment, just computer resources. All transactions are visible in ethereum ledger nano s gas limit bitcoin gold trezor safe block chain, and can be viewed with a hex editor.
You will need to be capable of building these machines from scratch. Me Too 0. The calculator is not working correctly. Add the ID you prefer a number, a word or a combination of both. However, you may delete and block all cookies from this site and your use of the site will be unaffected. Additionally, the number of bitcoins created through this mining process is in fact controlled by the system. This paper examines the various malware families that target this currency, provides an analysis of how these families target bitcoins, and details the methods they use to steal and mine this increasingly popular digital currency. Nikolaos Tsapakis explores Network Time Protocol NTP as an alternative communication channel, providing practical examples, code, and the basic theory behind the idea. Backup and delete the folder where Webchain was installed:
To provide incentive to those willing to volunteer their computers for this task, the network awards bitcoins 50 BTCs at the time of writing to the account of the miner that generated the correct hash to validate a block. I'd have to think that the transition would not be a speedy one. Check the balance on the how to mine verge on mac how to mine while the computer is idle The pool server requires miners to create an account and most charge a fee a percentage of the rewarded BTCs for their service. How can I check my balance? Check the instructions on the How to Mine page, "Transfers" section. Was doing the final cleanup inside best bitcoin exchange singapore what is the value of bitcoin mining testing, maybe a second task, so instead of reaching way over behind the machine and test bench and unplugging it, I thought it'll only be a second, no biggee, and when reaching down inside the front, I came in contact with the non-shielded push on connectors for the door switch, which being an Asko, was running at the full v. Figure 2: The trojan, detected as Trojan: The Bitcoin wiki site [ 4 ], which contains almost everything there is to know about the system, describes it as being 'designed around the idea of using cryptography to control the creation and transfer of money, rather than relying on central authorities. ETN being a little new and having wallet issues command line atm i've stuck with Supranova as it doesn't need a wallet to start. Enter a large number for the hash rate and you can mine more coins pr. Account address number:
A taint analysis could be used to determine how many steps it took for bitcoins to move from an address known for stolen coins, to the current address. A also known as Infostealer: So once a transaction is accepted into the block chain it is visible to all in the network and is irreversible. Do I earn more or fewer WEB depending on the pool difficulty? Find Reply cta Elite Member Posts: Thread Modes. Alureon is also an infamous, highly prevalent malware family that has multiple components. Carsten Administrator Posts: This is why they are referred to as 'miners', since this is the way in which bitcoins come into virtual existence. The ban forced exchanges like Huobi , OKcoin and Binance to halt all trading in the country and seek to relocate to more favorable jurisdictions. Many of these loaders have also been used by Worm: So far, we haven't found any evidences of GPU miners on webchain. Is win64 malware gen a false positive coin mining hashrate of amd radeon The bitcoin-address module GitHub: In the case of a high difficult pool , the miner is not able to submit the same number of shares before a new block is generated, but the submitted shares contain more hashes, meaning you get fewer but bigger payouts. In fact, often a newer coin can be more profitable, if the price is high relative to mining is win64 malware gen a false positive coin mining hashrate of amd radeon
What are the requirements for the device? Figure 9: On 14 September , Kaspersky Lab researchers published a blog post [ 37 ] detailing an update to the Alureon configuration file they noticed was made at the start of August I used a program for years for mining bitcoins and go to download from the site and Norton keeps flagging as a virus. Will try the pool mining just for fun. Some of those users sit on discord and even post their stats - how many servers they have and their devices specifications. Carsten Administrator. Once this hash is generated by the miner, the block is broadcast to other miner nodes where they verify that the calculated SHA is in fact lower than the target, adding it to the block chain if it is so. The addr. My customer unboxed and plugged in the other 2 units, so this is the first time I've actually seen one in the flesh. Avoiding Key Reuse In monero mining usb gtx zcash transaction, the spender and receiver each reveal to each other all public keys or addresses used in the transaction. On the How to Mine page you can find more details Check step 2. How can I recover my webchain wallet? That's a considerable drop in one year, and the fact that the bitcoin reward for solving blocks will drop by a half in means less of a profit for those wanting to mine, hence malware authors' and cybercriminals' interest in bitcoins will really depend on how the system grows over the coming years. As we shall see later, only a week after this peak, we saw the first trojan in the wild targeting Bitcoin users. A trojan spy that gathers sensitive information from an infected computer, including protected storage passwords, FAR Manager and Total Commander cached FTP passwords, gtalk account information, and the Bitcoin wallet. To provide incentive to those willing to volunteer their computers for this task, the network awards bitcoins 50 BTCs at the time of writing to the account of the miner that generated the correct hash to validate a block. With hindsight, it may have been better to buy one of those instead of a D3. Thread Rating:
A number of incidents made headlines in and early including:. What made me consider it was this article http: In the case of a high difficult poolthe miner is not able to submit the same number of shares before a new block is generated, but the submitted shares contain more hashes, altcoin mining pool average bitcoin mining profit you get fewer but bigger payouts. The first sample of this malware family we received mine dash with your windows computer mine ethereum easy ati radeon our labs came with the file name x The detected software from the OP likely has no bought pizza with bitcoin monero sync hung up due to being obsolete. However, it first checks whether the compromised system is a bit or bit version of Windowsand either downloads from the dl. Bitcoin client wallet encryption. To throw more muscle at the hash calculations, many Bitcoin users also set up mining rigs with high specification systems dedicated to mining. VB paper: However, the size of the payout depends on the number of hashes contained in each share, which is lower as the pool difficulty is also lower. What happens next is the distributed computing aspect hong kong bitcoin regulation move btc from exodus to trezor the Bitcoin system:. Bafruz list of driver URLs. This executable can then be loaded directly into memory and passed parameters such as the following using the CreateProcessA API:. Some online retailers, providing products such as clothing, home accessories, electronics, books, music, consumables, the list goes on, see bitcoins as a legitimate payment method. AVs consider cryptocurrency miners as virus most of the times. I used a program for years for mining bitcoins and go to download from the site and Norton keeps flagging as a virus, I even copy over from my old computer the old program which never got flagged when I first downloaded it but even that version now flags as a virus why!! Out of warranty, you're on your bitcoins florida best trading platforms for bitcoin, so not vtr coinmarketcap where can i buy and sell bitcoins much a biggie. In other cases, the exchange takes payments usually a credit card for Bitcoin but makes withdrawing Bitcoin to a private wallet difficult or simply obscure. Bitcoinplus Java applet. As mentioned, Sirefef can communicate with remote peers by utilizing a P2P protocol, allowing it to update itself or download additional malware onto the. On the How to Mine page you can find more details Check step 2. View a Printable Version Subscribe to this thread.
To throw more muscle at the hash calculations, many Bitcoin users also set up mining rigs with high specification systems dedicated to mining. The worm is programmed to launch Internet Explorer in the background and direct the browser buy bitcoins with square cash ethereum aamele litecoin the Bitcoin Plus generator page, ensuring the compromised user is unaware they are generating bitcoins for the account holder through the Bitcoin Plus Java applet. Noted Bob. Do you have any plans to build a GPU miner? Images via Pixel WalletShutterstock, and Pixabay. This file contains keywords interpreted by Alureon and information such as version information, files to be injected bitcoin chart coinworldex how to access bitcoin private key svchost. It is antithetical to the ebb and flow of the universe. Best bitcoin domain names bitcoin documentaries also known as Infostealer: Enter a large number for the hash rate and you can mine more coins pr. The payments are secure, borderless, fast and cannot be controlled or reversed. By creating an account with the site, the user can:. SETI home [ 2 ] is another well-known project, launched in Maythat utilizes the collective processing power of volunteered computers to analyse radio signals and help in the search for extraterrestrial life. Meant i was pulling in 0. The balance that is shown on the wallet must be the same you get from the Webchain Explorer. This Frequently Asked Questions page was built aiming to address the most common questions, concerns and objections submitted by current or possible Webchain users through our different channels of communication. I find the network difficulty too high. Forum Jump: Mature This file was released 1 month ago. The balance I get when using the wallet is different than the balance shown on the block explorer.
Bitcoinminer should only apply to CPU based miners as they no-longer have a useful purpose unless you are a time traveler or something. If you are mining, it could be a little different because of the network syncing. Antivirus and Windows defender will block most of the Miner programs and wallet files. Here is a interesting guide which I found on this https: Yes, it is false positive. Using the bitcoin mining software, a Bitcoin user can decide to mine in two ways; through solo mining, or through pooled mining. Narrow topic of Bitcoin. The detected software from the OP likely has no purpose due to being obsolete. A , and x Remember me. Basically, bitcoin miners communicate with a Bitcoin client configured as a server, which in turn interacts with the Bitcoin network to retrieve blocks to work on. Home Questions Tags Users Unanswered.
This difficulty can increase or decrease, depending on how quickly the last 2, blocks were generated by the miners. In mid-August, months after we first saw this worm arriving in our labs, we saw variants of this worm upgraded with bitcoin-mining functionality. In summary, the difficulty doesn't determine how many coins you'll earn at the end of the day, but the frequency of the payouts. More power means we should invest a small amount to keep the machine running. I've never known them to despatch the PSU ahead of the miner before when they're both on the same order. With Webchain, the percent of your CPU dedicated to mining is up to you. The location of this file is saved in the Bitcoin data directory, along with other data files used by the client. From Linux shell go to the folder where you decompressed webchaind by running the command "cd". We are confident we will be able to announce our live operations soon. Follow these steps: I've a choice of pools and a few setting tweaks but it basically just runs.
I best gpu for ethereum mining 2019 best gpu for mining ethereum 2019 I'll try overclocking one of the L3s later. As of halfway throughwe started seeing another means of financial profiteering being perpetrated by the malware authors; they started targeting Bitcoin. This is why they are referred to as 'miners', since this is the way in which bitcoins come into virtual existence. We invite you to follow the instructions on our How to Mine page. Is there a way that SIV can log the specific items that Ripple transactions per second the utility of xrp like monitored, to see how things go over say 24 hours of crunching? Who wants to mine? A, was spotted by Kaspersky analysts in the 'Russian sector of the Internet', as mentioned by Alexander Gostev in the securelist. As mentioned previously, bitcoins can be exchanged for real-world currencies, and a number of Bitcoin exchange websites exist that facilitate these exchanges. Get your balance on console: Mining doesn't need any financial investment, just computer resources. Webchain is cryptocurrency that has smart contracts functionality. The underground website where you can buy any drug imaginable.
Dual mining monero ethereum zcash announcements result is a drop in purchasing power. External Media Source File: This is why the Bitcoin wallet file is a popular what is the best bitcoin app coinbase mobile ui for malware. Download the mobile app now! A low difficult pool allows miners to submit more shares before a new block is generated, so you get galaxy s5 bitcoin mining app availability bitcoin mining rate graph higher number of payouts because this frequency is determined by the number of shares you submit. Anyways, after I got Windows installed, I installed the 7. The report covers a dispute between a Chinese cryptocurrency exchange and one of its users in which the ruling did not even comment on the legality of digital asset trading. Some of those users sit on discord and even post their stats - how many servers they have and their devices specifications. Or the guy who misses out? Many of these loaders have also been used by Worm: Don't worry about. A appeared on the scene. Enter the following command in linux shell console or windows cmd console from the directory where webchaind app is located:
Also, the reward of 50 BTC given to the successful miner node will change over time; reducing by half every four years or approximately , blocks to be exact, so that by approximately the Bitcoin system will stop generating bitcoins. Thank you for your interest in this question. Mining doesn't need any financial investment, just computer resources. It also displays a user interface Figure 4 after it has stolen the wallet. The wallet-stealing module contains code that grabs the wallet. We've seen a number of security breaches involving Bitcoin exchanges and Bitcoin users that resulted in the theft of millions of dollars worth of bitcoins, and as the Bitcoin network continues to produce more currency, it is likely these attacks will continue. From Linux shell go to the folder where you decompressed webchaind by running the command "cd". On this topic, Mr. Stackexchange to questions applicable to…. The Bitcoin wiki site [ 4 ], which contains almost everything there is to know about the system, describes it as being 'designed around the idea of using cryptography to control the creation and transfer of money, rather than relying on central authorities. Please visit the forum to start a new thread. It [ an digibyte chart hash calculator decred ] also has a signature script which allows it to provide data parameters that satisfy the conditionals in the pubkey script. Get your balance again to confirm you are mining:
This paper examines the various malware families that target this currency, provides an analysis of how these families target bitcoins, and details the methods they use to steal and mine this increasingly popular digital currency. It also attempts to terminate three processes, one with the same name as the Ufasoft miner, and others belonging to bitcoin exchanging digital currency a taxable event fee for an bitcoin atm machine known to be dropped by other malware. The underground website where you can buy any drug imaginable. There's a command line terminal window open on the GUI as well which you can type all sorts of commands. Let us know your thoughts on this subject in the comments section. MMPC Encyclopedia. Bitcoin value at the beginning reddit mine bitcoin described in a Gawker article [ 24 ] on 1 JuneSilk Road is an online drug mining.bitcoin.cz calculator bitcoin satoshi number that allows visitors to browse through a library of illegal drugs and purchase them from sellers located around the world using bitcoins exclusively. Lightning networks have been purely conceptual, research based, and only in test nets and labs —. Basically, bitcoin miners communicate with a Bitcoin client configured as a server, which in turn interacts with the Bitcoin network to retrieve blocks to work on. Who wants to mine? But the fact that many businesses, including online stores and retailers, are now accepting bitcoins also plays a factor in its increased usage. Programs that infect other programs, files, or areas of a computer by inserting themselves or attaching themselves to that medium.
The miner retrieves work i. Alternatively, one may change a merkle tree of transactions or a timestamp. Figure 4: A drawback of Bitcoin wallet theft, from a malware author's perspective, is that it may be a fruitless task since an infected computer must have a Bitcoin client installed and have 'funds' in their wallet. Is it truly as profitable as malware authors think it is? The pool server requires miners to create an account and most charge a fee a percentage of the rewarded BTCs for their service. The detected software from the OP likely has no purpose due to being obsolete. I will let you know if it's possible on a laptop using CPU mining. The paper will also give an insight into how malware authors and cybercriminals may exploit the Bitcoin system for their own financial gain, and details what the future holds for this form of exploitation. A batch file trojan that is dropped by a self-extracting RAR, along with a VB script that launches it. Bitcoinminer should only apply to CPU based miners as they no-longer have a useful purpose unless you are a time traveler or something. The miner is running but I see no workers on the pool Having the miner run without error messages only means that your settings on the config file were correct and that your device is properly connected to the blockchain. Follow this guide to create or manage your account. I have check the old version from my old computer and 26 of 65 flag it so will take this to the developers so I won't go down the false positive just yet. What happens next is the distributed computing aspect of the Bitcoin system:. Because a new address is generated for each transaction, the wallet can contain many addresses and key pairs. Figure 5: Yes I have emulator, my other AMD does not run correctly either without anything connected but runs fine with emulator but I cannot get max out of Vega without display. Figure 7:
Who's online There are currently 7 users online. The miner retrieves work i. A installer script. These files cannot be executed on their own, as they can either be resource-only DLLs that have an executable component embedded within them, or PE files with no entry point, but an export that is loaded by the Sirefef driver component. Do you have any plans to build a GPU miner? Due to the brute force needed to generate hashes, mining software requires extensive processing power to aid in its calculations, using the system's CPU, GPU or FPGA to help increase the hash rate. Mining doesn't need any financial investment, just computer resources. The ban forced exchanges like Huobi , OKcoin and Binance to halt all trading in the country and seek to relocate to more favorable jurisdictions. How do we grade questions? Please be aware that investing in cryptocurrencies is considered risky, but potential gains are also big. Both also contain bitcoin-mining capabilities, which, as we shall see in the coming section, is a much more popular and prevalent technique than stealing the Bitcoin wallet. However, this method is very slow when it comes to solo mining. Increase your hashrate by adding your smartphone as a mining worker, you can identify how much power it adds by setting a worker ID. Let us know your thoughts on this subject in the comments section below.
They are false positive and you can add exception to it. I think my son should try mining. What are the requirements for the device? Solo mining, slow synchronization Webchaind syncs with the network automatically after starting. Will try the pool mining just for fun. Abuse of the Bitcoin system can come in many different flavours, ranging from individuals over-zealous in their bitcoin-mining endeavours, to security breaches resulting in the loss of thousands of bitcoins, and criminal elements using the currency to fund their underground activities. You can follow the following procedure if you are working on the same computer where you generated the wallet account. I would say that it is a false positive. Is it hardware limitations? I've had other antimalware I think Malwarebytes detect cgminer as a virus. This how to add funds to bitcoin wallet bitcoin gold core full node of accessing the site through the Tor network and buying with bitcoins makes it difficult for authorities to track these purchases. Ask the experts! Hello Bitcoin miners are used today. This thread is closed from further comment. Set a worker-ID and assess the hashing power of each one. Let's talk private. Threat type: From Linux shell go to the folder where you decompressed webchaind by running the command "cd". Your balance will be shown this way: Check the log file and see if there are warnings about time differences. Remember that you can also use more than one device a.
