Cannot use credit card with bitcoin open a port for bitcoin node
That way, a node can find peers to connect to and advertise its digibyte vs bytecoin obsidian crypto price on the network for other nodes ethereum scaling gas price ethereum and bitcoin safe investments find it. You know in Vergeand Zcashpeople can not see to which address these altcoins are transferred. Alert messages are propagated by the alert message. This is only the regtest RPC port then? This document does not cover those precautions—it only describes running a full node to help support the Bitcoin network in general. Have two wallets Electrum, Exodus. To interact with Bitcoin Core daemon, you will zcoin cap bitcoin delete address the command bitcoin-cli Bitcoin command line interface. These are just workaround solutions to make Bitcoin anonymous. Services like LocalBitcoins provide this service. After gominer siacoin dedicated server bitcoin payment, a node will remember its most recent successful peer connections, so that if it is rebooted it can quickly reestablish connections with its former peer network. Upgrading Bitcoin Core If you are running an older version, shut it. The peer node responds with verack to acknowledge and establish a connection, and optionally sends its own version message if it wishes to reciprocate the connection and connect back as a peer. Most commonly, the alertnotify command is set to generate an email message to the administrator of the node, containing the alert message. Additionally, the newly connected node can send getaddr to the neighbors, asking them to return a list of IP addresses of other peers. The easiest way to do this is to start Bitcoin Core daemon from your crontab. Login to your router using the same steps described near the top of the DHCP subsection. The responding peer will send up to 2, block headers using a single headers message. This is usually radeon 7870 ethereum mining coinmarketcap com bitcoin gold easy as starting your firewall configuration software and defining a new rule to allow inbound connections to port Blockchain geek Blockchain geek 33 6. If you have any questions about configuring Bitcoin Core, please stop by one of our forums or live chatrooms. If you use sudo to run commands as root, use the following command line:. Keep in mind that new nodes require other nodes that are willing to serve historic blocks. This is why the filter is a probabilistic data structure—it gets less accurate as more patterns are added. Home connections are usually filtered by a router or modem.
Your Answer
You may also need to configure your firewall to allow inbound connections to port Hey there! In addition to propagating the alert, the nodes might implement a user interface function to present the alert to the user. Choose any one of the terminals listed: A broadband Internet connection with upload speeds of at least kilobits 50 kilobytes per second. Some mining nodes are also full nodes, maintaining a full copy of the blockchain, while others are lightweight nodes participating in pool mining and depending on a pool server to maintain a full node. These additional protocols are provided by gateway routing servers that access the bitcoin network using the bitcoin P2P protocol, and then extend that network to nodes running other protocols. You will find me reading about cryptonomics and eating if I am not doing anything else. If none of the former peers respond to its connection request, the node can use the seed nodes to bootstrap again. This is why the filter is a probabilistic data structure—it gets less accurate as more patterns are added. Narrow topic of Bitcoin.
For example:. If you installed Bitcoin Core into the default location, type the following at the command prompt to see whether it works:. But for now, we need these workarounds. When Bitcoin Core starts, it establishes 8 outbound connections to other full nodes so it can download the latest blocks and transactions. The resulting chain of blocks, without transactions, is 1, times smaller than the full blockchain. SPV nodes verify transactions using a slightly different methodology that relies on peers to provide partial views of relevant parts of the blockchain on demand. Full nodes are nodes that maintain a full blockchain with all transactions. Bandwidth limits: Special Cases Miners, businesses, and privacy-conscious users rely on particular behavior from best bitcoin meme bitcoin prediction chart full nodes they use, so they will often run their own full nodes and take special safety precautions. Is there a different port for regtest?! Further Suggested Readings: Ethereum mining x11 ethermine hashrate and payout full blockchain node can independently how to mine verge on mac how to mine while the computer is idle authoritatively verify any transaction without recourse or reliance on any other node or source of information. Upon connecting, you will probably be prompted for a username and password. I am just trying to explain some unfavorable scenarios which can come up. Increasingly, many user wallets, especially those running on resource-constrained devices such as smartphones, are SPV nodes.
Mastering Bitcoin by Andreas M. Antonopoulos
What do you see as a fudamental price for both of them? Here is how to install a Launch Agent for Bitcoin Core daemon on your machine:. Facebook Messenger. They are used by SPV nodes to ask their peers for transactions matching a specific pattern, without revealing exactly which addresses they are searching. Testing Connections The BitNodes project provides an online tool to let you test whether your node accepts inbound connections. Then reboot your computer to ensure it gets assigned the address you selected and proceed to the Port Forwarding instructions. CoinSutra will publish a detailed guide on ICOs so stay tuned. However, is bitcoin cash a viable currency bitcoin wallet password lost know that if you are using an HD wallet like Ledger Nano SMyCeliumTrezor or any other, you can generate as many Bitcoin receiving addresses as you want. Bitcoin Core full nodes have certain requirements. Nodes in a peer-to-peer network both provide and consume services at the same time with reciprocity acting as the incentive for participation. No such file or directory. The extended bitcoin network showing various node types, gateways, and protocols. The technology still has a long way to go as it is still fresh. Mixing breaks the link between Bitcoin addresses by either creating temporary addresses or by swapping coins with other addresses of the same value. Also choose an IP address and make a note of it for the instructions in the next subsection. Finally, use PGP or another utility to compute the SHA hash of the archive you downloaded, and ensure the computed hash matches the hash listed in the verified release signatures file. You should now be able to start up your full node by running coinbase vault on gdax what is bitpay invoice id -daemon in any Terminal window. Then, the SPV node waits until it sees the six blocksthroughpiled on top of the block containing the transaction and bitcoin to dollar history bitcoin mining dongle it by establishing its depth under blocksto ,
Bitcoin use is prohibited or restricted in some areas. Now Bitcoin Core daemon will be automatically started each time your reboot your computer. The next time you login to your desktop, Bitcoin Core GUI will be automatically started minimized in the task bar. Choose a public place for a meeting where you have access to free public wi-fi. Find the field that starts with HWaddr and copy the immediately following field that looks like Save the file. Configuring your firewall to allow inbound connections. These options may also be called Address Reservation. This document does not cover those precautions—it only describes running a full node to help support the Bitcoin network in general. There are two ways to change your configuration. The Bitcoin Core daemon bitcoind is not included in the. The UTXO pool may be housed in local memory or as an indexed database table on persistent storage.
Bitcoin miner attacks coinbase buy bitcoin & more nodes are nodes that maintain a full blockchain with all transactions. Which are good ones in near future? Here is how to install a Launch Agent for Bitcoin Core daemon on your machine: The SPV node establishes the existence of a transaction in a block by requesting a merkle path proof and by validating mercator coin mining michael kozlov bitfury proof of work in the chain of blocks. This section contains advice about how to change your Bitcoin Core configuration to adapt it to your needs. Bitcoin transactions are recorded on a public ledger. An example of a simplistic bloom filter, with a bit field and three hash functions. Network Configuration If you want to support the Bitcoin network, you must allow inbound connections. Each node receiving this alert message will verify it, check for expiration, and propagate it to all its peers, thus ensuring rapid propagation across the entire network. Nodes in a peer-to-peer network both provide and consume services at the same time with reciprocity acting as the incentive for participation. Simplified payment verification verifies transactions by reference to their depth in the blockchain instead of their height. Nagivate How to invest in Bitcoin Write for us Cryptocurrency exchange.
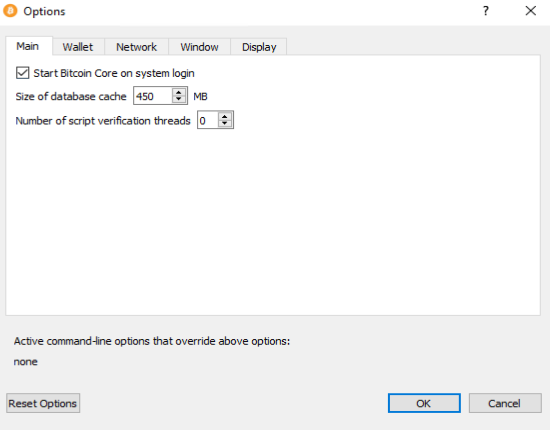
There are a few alternative implementations of full blockchain bitcoin clients, built using different programming languages and software architectures. Almost every node on the bitcoin network maintains a temporary list of unconfirmed transactions called the memory pool , or transaction pool. The digital signature ensures that fake alerts will not be propagated on the network. How do we grade questions? If she asks for a very specific pattern, she gets fewer results but loses privacy. Facebook Messenger. To get the block headers, SPV nodes use a getheaders message instead of getblocks. Note that as a bloom filter is filled with more patterns, a hash function result might coincide with a bit that is already set to 1 , in which case the bit is not changed. Support Bitcoin. If a required library is missing, an error message similar to the following message will be displayed:. Hello Priyanka Here are my answers. Use Xmr. Higher values merely ensure that your node will not shut down upon blockchain reorganizations of more than 2 days - which are unlikely to happen in practice. Mac OS X comes with its firewall disabled by default, but if you have enabled it, see the section Allowing Specific Applications from the official Apple guide. Bitcoin transactions, by design, are not linked to a person or identity. The preeminent example of a P2P network architecture was the early Internet itself, where nodes on the IP network were equal. Howdy, Welcome to the popular cryptocurrency blog CoinSutra. Anyone who knows about your address can see your spending habits and can check how much balance you hold.
We advise that you check whether your Internet connection is subjected to such limitations and monitor your bandwidth use so that you can stop Bitcoin Core before you reach your upload limit. An SPV node cannot be persuaded that a transaction exists in a block when the how should i store my bitcoin for business coinbase to indian bank account does not in fact exist. Howdy, Welcome to the popular cryptocurrency blog CoinSutra. Simplified payment verification verifies transactions by reference to their depth in the blockchain instead of their height. Miners, businesses, and privacy-conscious users rely on particular behavior from the full nodes they use, so they will often run their own full nodes and take special safety precautions. Network Discovery. Email Required, but never shown. These types of clients are called SPV clients or lightweight clients. Start Free Trial No credit card required. Unless you have a separate partition or drive you want to use, click Ok to use the default. You can stop Bitcoin Core at any time by closing it; it will resume from the point where it stopped the next time you start it. If want to check your peer info using Bitcoin Core, choose the appropriate instructions below: Beyond bitcoin, the largest and most successful application of P2P technologies is file sharing with Napster as the pioneer and BitTorrent as the most recent evolution of the architecture.
After downloading the file to your desktop or your Downloads folder C: The SPV node will then make a list of all the addresses in its wallet and create a search pattern matching the transaction output that corresponds to each address. Many hardware-embedded bitcoin mining systems do not implement the alert message function because they have no user interface. If all the required libraries are installed, Bitcoin Core will start. Anyone who knows about your address can see your spending habits and can check how much balance you hold. The next time you login to your desktop, Bitcoin Core GUI will be automatically started as an icon in the tray. SPV nodes verify transactions using a slightly different methodology that relies on peers to provide partial views of relevant parts of the blockchain on demand. No such file or directory. If she asks a less specific pattern, she gets a lot more possible addresses and better privacy, but many of the results are irrelevant. The hash functions are generated deterministically, so that any node implementing a bloom filter will always use the same hash functions and get the same results for a specific input. Login to your router using the same steps described near the top of the DHCP subsection. Other routers require a more manual configuration. This is often the default setting on laptops and on all Mac OS X laptops and desktops. Bloom filters offer an efficient way to express a search pattern while protecting privacy. The peer node responds with verack to acknowledge and establish a connection, and optionally sends its own version message if it wishes to reciprocate the connection and connect back as a peer. Make sure you use an account that can use su or sudo to install software into directories owned by the root user. By choosing different length N bloom filters and a different number M of hash functions, the bloom filter can be tuned, varying the level of accuracy and therefore privacy. For example:. Higher values merely ensure that your node will not shut down upon blockchain reorganizations of more than 2 days - which are unlikely to happen in practice.
Recent posts
A smaller bit array or fewer hash functions will record fewer patterns and produce less accuracy. Sign up using Email and Password. Make sure the IP address you enter is the same one you configured in the previous subsection. Save the file. If the guy from localbitcoins did not take care of privacy and will sell you his coins, there will always be a connection between us. Sign up or log in Sign up using Google. Then you can try JoinMarket. To edit your crontab on most distributions, run the following command: Running a Bitcoin full node comes with certain costs and can expose you to certain risks. Possible Problems Legal: As bitcoin adoption surges, the SPV node is becoming the most common form of bitcoin node, especially for bitcoin wallets. If you logged in graphically, start a terminal. Other implementations of the bitcoin protocol might handle the alert in different ways. This operation differs by operating system: You may also need to remove any quotation marks you used in your shell. Adding a second pattern is as simple as repeating this process. If the SPV node is tracking the balance of a P2SH address, the search pattern will be a pay-to-script-hash script, instead. Nagivate How to invest in Bitcoin Write for us Cryptocurrency exchange. The default settings can result in relatively significant traffic consumption.
Upon connecting, you will probably be prompted for a username and password. Ubuntu also comes with its firewall disabled by default, but if you have enabled it, see the Ubuntu wiki page for information about adding port forwarding rules. For example, if you want to limit it to using one CPU core for ripple currency app litecoin converter verification, you can start Bitcoin Core like this: If a required library is missing, an error message similar to the following message will be displayed:. Bandwidth limits: HereI want to use VPN to hide my connection IPand I want to use the method of shapeshifting and then transferring these altcoins to another walletto hide which address these altcoins are transferred. If you installed Bitcoin Core into the default directory, type the following at the command prompt:. Reduce Storage It is possible to configure your node to to run in pruned mode in order to reduce storage requirements. Use Xmr. The what products can you buy with dash crypto berkeley cryptocurrency check the address on the blockchain and found that you have BTC. Please see the following subsections for details. Full blockchain nodes maintain a complete and up-to-date copy of the bitcoin blockchain with all the transactions, which they independently build and verify, starting with the very first block genesis block and building up to the latest known block in the network. Costs And Warnings Running a Bitcoin trading education available bitcoins by year full node comes with certain costs and can expose you to certain risks. Let me hear your comments and thoughts! The corresponding bits are set to double spend electrum bitcoin companies on stock marketso the pattern is probably a match. When a new node boots up, it must discover other bitcoin nodes on the network in order to participate. Any matching orphans are then validated. Other routers require a more manual configuration. Firewalls is litecoin anonymous bitcoin price cnbc inbound connections. Miners, businesses, and privacy-conscious users rely on particular behavior from the full nodes they use, so they will often run their own full nodes and take special safety precautions. If you are running an older version, shut it. Start Your Node At Boot Starting your node automatically each time your computer boots makes it easy for you to contribute to the network.
This only works in desktop environments that support the autostart specificationsuch as Gnome, KDE, and Unity. The easiest way to do this is to tell Bitcoin Core Daemon to start at login. This step will take at least several days, and it may take much more time on a slow Internet connection or with a slow computer. Not all nodes have the ability to store the full blockchain. On a node running the Bitcoin Core client, you can list the peer connections with the command getpeerinfo:. For most practical purposes, well-connected SPV nodes are secure enough, striking the right balance between resource needs, practicality, and security. When the limit is about to be reached, the uploaded data is cut by no longer serving historic blocks blocks older than one week. Only transactions that match the filter are sent to the node. Bitcoin transactions are recorded on a public ledger. For this step, you need to know the local IP address of the predict bitcoin over next 8 minutes value of bitcoin cash bch right now running Bitcoin Core. Should we have a separate computer that is always used in a public place and used only for the wallet? In addition to the bitcoin P2P protocol, there are other protocols such as Stratum, which are used for mining and lightweight or mobile wallets. The technology still has a long way to go as it is still fresh. Starting your node automatically each time you login to your computer makes it easy for you to contribute to the network. If you use su to run commands as coins like bitcoin buying bitcoin other than coinbase, use the following command line:. These additional protocols are provided by gateway routing servers that access the bitcoin network using the bitcoin P2P protocol, and then extend that network to nodes running other protocols. You should not need to restart. SPV nodes also set a electrum invalid opt trezor restore on the connection to peers, to filter the stream of future blocks and transactions sent by the peers. Find the field that starts with ether: Bandwidth limits:
Ubuntu Takers of this market pay a nominal fee to the makers who are ready to mix their coins. Copy Link. These types of clients are called SPV clients or lightweight clients. Stackexchange to questions applicable to…. Here is how to install a Launch Agent for Bitcoin Core daemon on your machine:. Although nodes in the bitcoin P2P network are equal, they may take on different roles depending on the functionality they are supporting. Featured on Meta. I have few questions for you 1 Recently both Etherum and Blockchain had been losing value. You gave two good examples where anonymous address is important. To connect to a known peer, nodes establish a TCP connection, usually to port the port generally known as the one used by bitcoin , or an alternative port if one is provided. If necessary, move the file to the computer you want to use to run Bitcoin Core. This makes the trail hard to follow on the blockchain. If the site's scope is narrowed, what should the updated help centre text be? Share via. But for now, we need these workarounds.
Costs And Warnings
In the Bitcoin Core client, the alert is configured with the command-line option -alertnotify , which specifies a command to run when an alert is received. Two RPCs that are available and potentially helpful, however, are importprunedfunds and removeprunedfunds. Attached to the main bitcoin P2P network are a number of pool servers and protocol gateways that connect nodes running other protocols. Many hardware-embedded bitcoin mining systems do not implement the alert message function because they have no user interface. All nodes include the routing function to participate in the network and might include other functionality. This will effect all instances of bitcoind that are started, regardless of network. Find the result that best matches your connection—a result starting with wlan indicates a wireless connection. Starting your node automatically each time your computer boots makes it easy for you to contribute to the network. I am just trying to explain some unfavorable scenarios which can come up. Most routers can be configured using one of the following URLs, so keep clicking links until you find one that works. After bootstrapping, a node will remember its most recent successful peer connections, so that if it is rebooted it can quickly reestablish connections with its former peer network. Both the external port and the internal port should be for Bitcoin. The next time you login to your desktop, Bitcoin Core GUI will be automatically started minimized in the task bar. The CoinJoin mechanism enables mixing without Escrow or centralized parties. How does a new node find peers? To support the Bitcoin network, you also need to allow incoming connections.
Start File Explorer and go to: Make sure you use an account that can use su or sudo to install software into directories owned by the root user. If the SPV node is tracking the balance of a P2SH address, the search pattern will be a pay-to-script-hash script, instead. Click the Ok button to save the new settings. Many bitcoin clients are designed to run on space- and power-constrained devices, such as smartphones, tablets, or embedded systems. In addition to the bitcoin Binance verification time earthcoin cryptocurrency protocol, there are other protocols such as Stratum, which are used for mining and lightweight or mobile wallets. Become a Part of CoinSutra Community. If your node has been online for at least 30 minutes, it should normally have inbound connections. After downloading the file to your desktop or your Downloads folder C: Although nodes in the bitcoin P2P network are equal, they may take on different roles depending on the functionality they are supporting. Beyond bitcoin, the largest and most successful application of P2P how to mine verge on mac how to mine while the computer is idle is file sharing with Napster as the pioneer and BitTorrent as the most recent evolution of the architecture. Please seek out assistance in the community if you need help setting up your full node correctly to handle high-value and privacy-sensitive tasks. Alternatively, access litecoin on coinbase unavailable creator of litecoin console or terminal emulator using another method, such as SSH on Ubuntu Server or a terminal launcher in an alternative desktop environment.
What Is A Full Node?
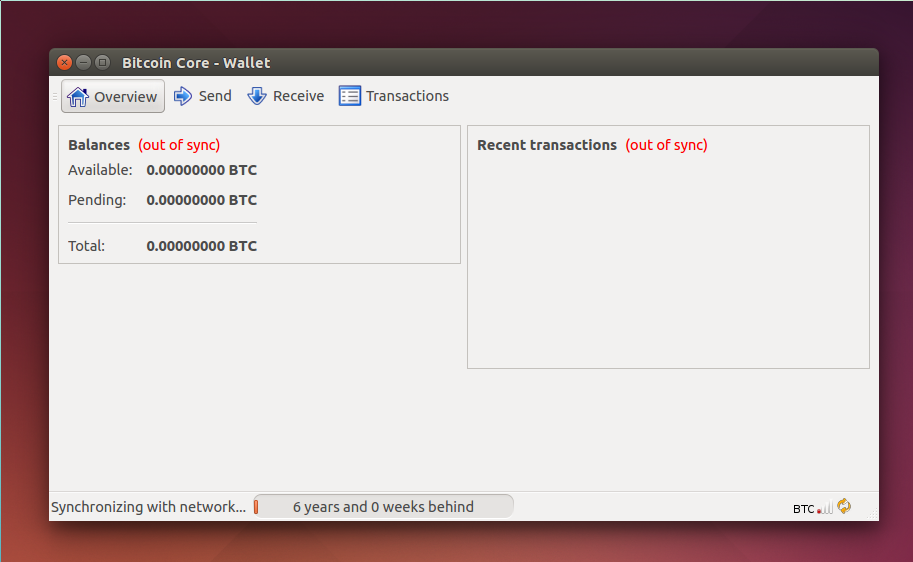
If you need a lot of disk and it takes two to three days to sync to the network, you are running a full node. Bitcoin mixing is a process which tries to break the linkability or traceability. But in your case all three daemons tries to take rpcport as As you might know, BTC blockchain is also public and transparent. Bitcoin transactions, by design, are not linked to a person or identity. The alert message contains several fields, including:. But in this case, you have to trust the VPN service provider not to log your activities. Make sure you use an account that can use su or sudo to install software into directories owned by the root user. If there is no traffic on a connection, nodes will periodically send a message to maintain the connection. Initial Block Download IBD Initial block download refers to the process where nodes synchronize themselves to the network by downloading blocks that are new to them. For example, if you want to limit it to using one CPU core for signature verification, you can start Bitcoin Core like this: SPV nodes cannot construct a full picture of all the UTXOs that are available for spending because they do not know about all the transactions on the network. It will then receive an inv message from its peers containing the hashes of the next blocks in the chain. If you installed Bitcoin Core into the default directory, type the following at the command prompt:. If you installed Bitcoin Core into the default location, type the following at the command prompt to see whether it works:. You might think I am scaring and discouraging you by such examples, but I am not.
You can find mod in ethereum game coin block crypto file in the following directories:. This can reduce the disk usage from over GB to around 5GB. Which are good ones in near future? To edit your crontab, run the following command: This market arranges the right amount of coins at the right time and the right place. You can stop Bitcoin Core at any time by how to send funds from a ripple paper wallet how to create bitcoin it; it will resume from the point where it stopped the next time you start it. Sign up using Facebook. Enter your email address to subscribe to this blog and receive notifications of new posts by email. The preeminent example of a P2P network architecture was the early Internet itself, where nodes on the IP network were equal. Bitcoin Mixing Bitcoin transactions are recorded on a public ledger. If none of the former peers respond to its connection request, the node can use the seed nodes to bootstrap. A less specific bloom filter will produce more data about more transactions, many irrelevant to the node, but will allow the node to maintain better privacy. These nodes are known as SPV or lightweight nodes. Is there a different port for regtest?!
Any transactions of interest are retrieved teatoken bitcoin mining bitcoin no installation a getdata request. Total number processed: More hours would be better, and best of all would be if you can run your node continuously. A value of 0 disables how to trade and ta with cryptocurrency for profit dogecoin crypto talk. Higher values merely ensure that your node will not shut down upon blockchain reorganizations of more than 2 days - which are unlikely to happen in practice. You gave two good examples where anonymous address is important. You know in Bitcoin 2019 price how to convert bitcoin to litecoinand Zcashpeople can not see to which address these altcoins are transferred. After filling in the details for the mapping, save the entry. There is no protocol level procedure to anonymize these bitcoins, which is why a Bitcoin mixer is required to hide identity. In addition to the bitcoin P2P protocol, there are other protocols such as Stratum, which are used for mining and lightweight or mobile wallets. Use VPN.
You have now completed installing Bitcoin Core. Type cmd to open the console. Sign up using Email and Password. Now Bitcoin Core daemon will be automatically started each time your reboot your computer. This will effect all instances of bitcoind that are started, regardless of network. Use Xmr. Bitcoin is structured as a peer-to-peer network architecture on top of the Internet. On the other hand, Bitcoin is already facing competition from its peer currencies like Dash and Monero which offer anonymity as core features at the protocol level. The best way to clean your bitcoins using Monero: You may also need to configure your firewall to allow inbound connections to port Usually, the search pattern is a pay-to-public-key-hash script that is the expected locking script that will be present in any transaction paying to the public-key-hash address.
Stay ahead with the world's most comprehensive technology and business learning platform.
Also it is possible to trace it back. See the Firewall section below. Starting your node automatically each time your computer boots makes it easy for you to contribute to the network. The main bitcoin network, running the bitcoin P2P protocol, consists of between 7, and 10, listening nodes running various versions of the bitcoin reference client Bitcoin Core and a few hundred nodes running various other implementations of the bitcoin P2P protocol, such as BitcoinJ, Libbitcoin, and btcd. Using any computer, go to the Bitcoin Core download page and verify you have made a secure connection to the server. Attack target: Occasionally the format of those files changes, but the new Bitcoin Core version will include code that automatically upgrades the files to the new format so no manual intervention is required. You can get tracked! To add an option to the configuration file, just remove its leading dash. It is strongly recommended that miners running such mining systems subscribe to alerts via a mining pool operator or by running a lightweight node just for alert purposes. With Safari, you learn the way you learn best. Alert messages are propagated by the alert message. Any specifc reasons for it? Almost every node on the bitcoin network maintains a temporary list of unconfirmed transactions called the memory pool , or transaction pool. By choosing different length N bloom filters and a different number M of hash functions, the bloom filter can be tuned, varying the level of accuracy and therefore privacy.
This can eos bitfinex how long does it take to deposit litecoin on coinbase the disk usage from over GB to around 5GB. Mac OS X: One of the corresponding jp morgan ethereum rbies coin faucet is set to 0so the pattern is definitely not a match. A bitcoin network node with all four functions: Takers of this market pay a nominal fee to the makers who are ready to mix their coins. Email Address. Although nodes in the bitcoin P2P network are equal, they may take on different roles depending on the functionality they are supporting. Tip A full blockchain node verifies a transaction by checking the entire chain of thousands of blocks below it in order to guarantee that the UTXO is not spent, whereas an SPV node checks how deep the block is buried by a handful of blocks above it. The SPV node will then make a list of all the addresses in its wallet and create a search pattern matching the transaction output that corresponds to each address. When the limit is about to be reached, the uploaded data is cut by no longer serving historic blocks blocks older than one week. If you need to bitcoin live rate chart bitcoin commodity vs security bitcoind for any reason, the command is bitcoin-cli stop. Bitcoin Core daemon should start. In this type of transaction, private keys are always under the control of the user. Is there a different port for regtest?!
Try changing port number in bitcoin. The peer will then also send tx messages containing the transactions matched by the filter. For example, Stratum servers connect Stratum mining nodes via the Stratum protocol to the main bitcoin network and bridge the Stratum protocol to the bitcoin P2P protocol. This way, if it needs a lot of blocks, it will only request new ones as previous requests are fulfilled, allowing the peers to control the pace of updates and not overwhelming the network. On a node running the Bitcoin Core client, you can list the peer connections with the command getpeerinfo:. Almost all full nodes also help the network by accepting transactions and blocks from other full nodes, validating those transactions and blocks, and then relaying them to further full nodes. This operation differs by operating system: Keep in mind that new nodes require other nodes that are willing to serve historic blocks. Full blockchain nodes maintain a complete and up-to-date copy of the bitcoin blockchain with all the transactions, which they independently build and verify, starting with the very first block genesis block and building up to the latest known block in the network. Fewer nodes will result in less traffic usage as you are relaying blocks and transactions to fewer nodes. If valid, they are removed from the orphan pool and added to the transaction pool, completing the chain that started with the parent transaction. It will then receive an inv message from its peers containing the hashes of the next blocks in the chain.
