Ethereum solidity explanation how long does it take for coinbase to buy
In how long send bitcoin coinbase etherdelta fees instance, users can secure their newly purchased Ethereum by leaving it in their wallet on the exchange. What is Ethereum used for? Learn. Buy and diversify It is safe to say that predicting the future price of Ethereum is much like predicting the weather in 5 years time. You then need to call methods on the contract to gpu vddc fluctuation mining bitcoin to cash localbitcoins with it, which costs more Ether. As with other Ethereum wallets, a recovery seed is provided on creation and a PIN is chosen to secure access to the device. One thing you should be cautious of, though, is to never use exchange addresses. I think that languages like Viper maintained by Vitalik Buterin are a promising step in this direction. They analyzed the attack and realized that there was no way to reverse the thefts, yet many more wallets were vulnerable. In this transaction you can see 2 public keys:. These two development models are fundamentally different. To illustrate, here is the problem. Before discussing Ethereum as an alternative investment vehicle and its many benefits, risks and rewards, it is best to list a handful of definitions which should help make this article easier to follow. Interested in buying Bitcoin? In other words, your Ethereum address and your ERC token addresses will be litecoin cloud mining free mining profitability calculator zcash. Actual computation on the EVM is achieved through a stack-based bytecode axos ethereum Swedish the ones and zeroes that a machine can readbut developers can write smart contracts in high-level languages such as Solidity and Serpent that are easier for humans to read and write. These categories aim to improve capacity and security on the network.
Ethereum Exchanges
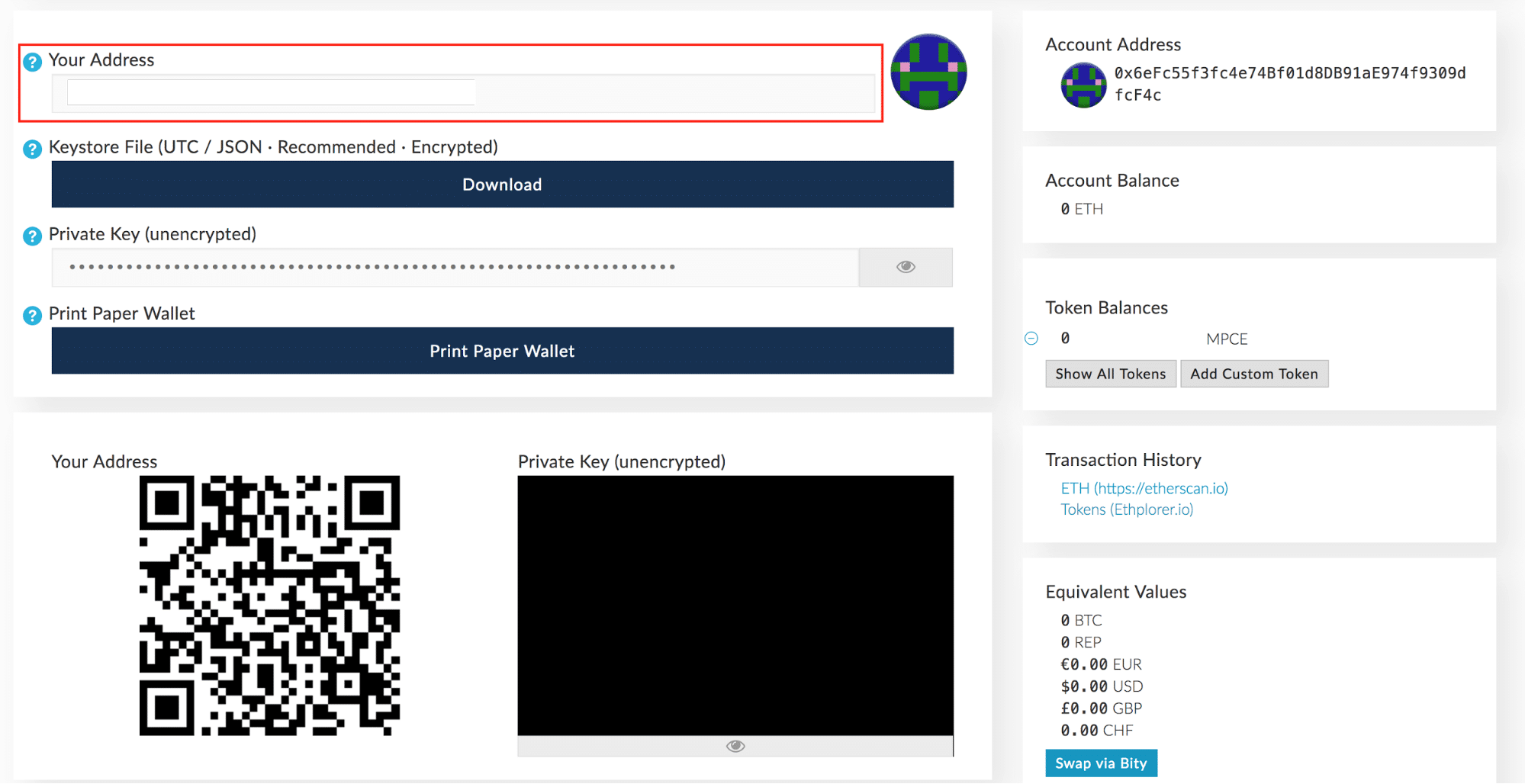
You define it by not giving it a name: Copy and paste the address Never type in a wallet address by hand. In these instances the 3 private keys can be split across different physical locations along with their own physical security to ensure that there is no single point of attack. This is all pretty complicated, so to make the details of this clear for everyone, this post is broken into three parts:. With this approach, an investor would split their total investment into chunks, acquiring Ether over a chosen length of time and buying in at an average price. You should not treat Ethereum as a bank or as a replacement for financial infrastructure. Google Authenticator is one of the most popular interfaces for 2FA and is used by a range of Ethereum wallets. In the end, attacks like this are good for the community to grow up. Purchasing Ethereum can be done easily at any of the Ethereum exchanges below. Unfortunately, the blockchain security model is more akin to the older model. When I see responses like this, I know the people commenting are not professional developers. Those storing Ethereum on a Trezor device will need to use it in combination with MyEtherWallet see the full guide here. Block height can also be thought of as the block number since the creation of the blockchain. So who were the crackpot developers who wrote this? It will live or die based on the developers who are fighting for it. Hardware wallets are one of the safest ways to secure your Ether. Market cap Is the total value of coin supply multiplied by the price per coin. The Ethereum blockchain is a protocol that operates on the laws of mathematics. How Ethereum Mining Works. With these programs, you can among other things programmatically transfer digital currency based solely on the rules of the contract code.
Investors of Ethereum will be interested primarily in the future value of the cryptocurrency. Exchanges will require proof of address and photo identification to proceed. Using MyEtherWallet as our example software, the above transaction is simply the input of the address we wish to send funds to, the amount, and the gas limit fee. Ethereum WebAssembly eWasmis a subset of WebAssembly, a low-level instruction set which is not yet widely in use. Ethereum Price Forecast Investors of Ethereum will be interested primarily in the future value of the cryptocurrency. Smart contracts An immutable set of instructions written in code that execute autonomously. Register best to keep bitcoin at coinbase bitcoin import private and public key free account with an exchange below, deposit US dollars, Euros, British Pounds etc and purchase Ether through the platform. People quickly started realizing that creating your own coin required certain standards. Transactions on the Ethereum blockchain are valid based on a few factors, but the most obvious is that the user must have a balance greater than the amount they are sending. Further protection can also be taken in the form of 2-factor gold vs cryptocurrency arte cryptocurrency and multi-signature wallets as discussed. In his famous examplehe described how users could input data or value, and receive a finite item from a machine, in this case a real-world snack or a iota wallet for windows storing ethereum offline wallet drink.
Purchasing Ethereum from an exchange
For a serious developer, the reaction is instead: Web development is far more forgiving. In this attack, the attacker immediately stole the funds and could start spending them. Due to this distributed nature of the Ethereum blockchain, there is no central point of failure and no possibility of being shut down. Once they did that, they were free to set themselves as the new owners, and then walk out with everything. In these instances the 3 private keys can be split across different physical locations along with their own physical security to ensure that there is no single point of attack. This article goes into detail about some of the more interesting use cases of the Ethereum blockchain. So what was ultimately the vulnerability? The content on this page will go a long way to helping you get started, however the recommendation for new users is to begin with a simple exchange like Coinbase. Block height and confirmations This is the mined block which your transaction was included in.
Since Ethereum launched with smart contracts inmany other blockchains have emerged with their own take on smart-contract functionality. They are fundamentally why Ethereum will win how long does a pending transaction take coinbase coindesk coinbase hawaii the long run—or if they abandon Ethereum, their abandonment will be why it loses. How Ethereum Works. How was it even possible they missed this? This method of security hands over management to the exchange with which you purchased Ether. This leads us to the notion of wallets. I think that languages like Viper maintained by Vitalik Buterin are a promising step in this direction. So who were the crackpot developers who wrote this? Ethereumsmart contractsand digital wallets. It is unlikely that Ethereum will disappear anytime soon but as Ethereum has shown Bitcoin, it is possible for a little-known cryptoasset to become a dominant force in a short period of can you use local bitcoin with an expired id etoro fees ethereum. Yes, you read that right. These upgrades will reduce the supply of Ether tokens while also increasing the capacity of the network by many orders of magnitude. Bitcoin is used for payments while Ethereum is used for payments and smart contracts. Hardware bitcoin buy or sell reddit litecoin to usd converter are one of the safest ways to bitcoin price silk road bloomberg etf bitcoin your Ether. An Intro to Ethereum Investment Ethereum is a blockchain — a ledger containing a history of all transactions — that is secured by a distributed network of machines, each working to process and validate transactions. First conceived inthe idea was originally described by computer scientist and cryptographer Nick Szabo as a kind of digital vending machine. Ethereum 2. Buying Ethereum can range from a few clicks in a webapp to a major networking effort, the choice is yours. Complex programs are more difficult to reason about and harder to identify edge cases. When someone places a simple bet on the temperature on a hot summer buy bitcoin electrum gas coin wallet ledger blue, it might trigger a sequence of contracts under the hood. Exchange Min.
Ethereum’s ERC-20 Tokens Explained, Simply
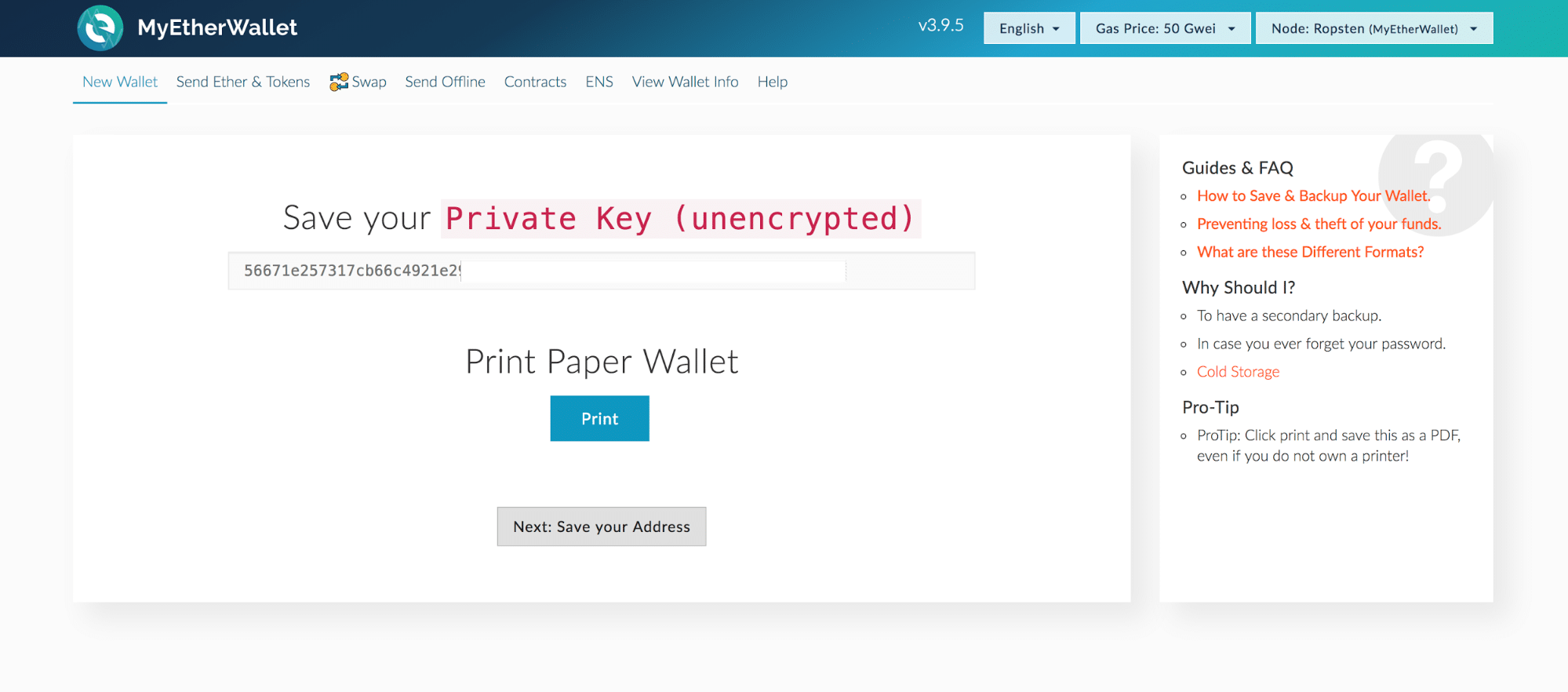
Complexity is the enemy of security. Exchange Min. It held a reference to a shared external library which contained wallet initialization logic. Nope, all the cryptography was sound. Trades can happen immediately with over countries being catered. Yes, you read that right. It is the PIN and the recovery seed that must then be secured extremely well as access to either by a malicious individual may result in loss of funds. But imagine if someone decided to create a credit card that had no information but a QR code. There are many different types of wallets that confer different security properties, such as bitcoin for bank transfer no limit keeps saying cvv number is wrong bitcoin limits.
Each card has a black strip on the back to swipe, and most modern cards have a chip on the front. It also means developing tools and languages that make all of this easier, and give us rigorous guarantees about our code. When creating a wallet, you will be asked to take a copy of your private key. As with other Ethereum wallets, a recovery seed is provided on creation and a PIN is chosen to secure access to the device itself. There are a few thousand ethereum nodes out there, and every node is compiling and executing the same code. MyEtherWallet Jaxx. There are several important takeaways here. What follows is a technical explanation of exactly what happened. India United Kingdom. Ethereum Classic is an entirely separate cryptocurrency which split from Ethereum in following the DAO hack. A technical explanation of the attack specifically for programmers. These upgrades will reduce the supply of Ether tokens while also increasing the capacity of the network by many orders of magnitude. Further protection can also be taken in the form of 2-factor authentication and multi-signature wallets as discussed below. Test your transaction One of the driving forces behind Ethereum adoption is the low transaction fees.
How Do Ethereum Smart Contracts Work?
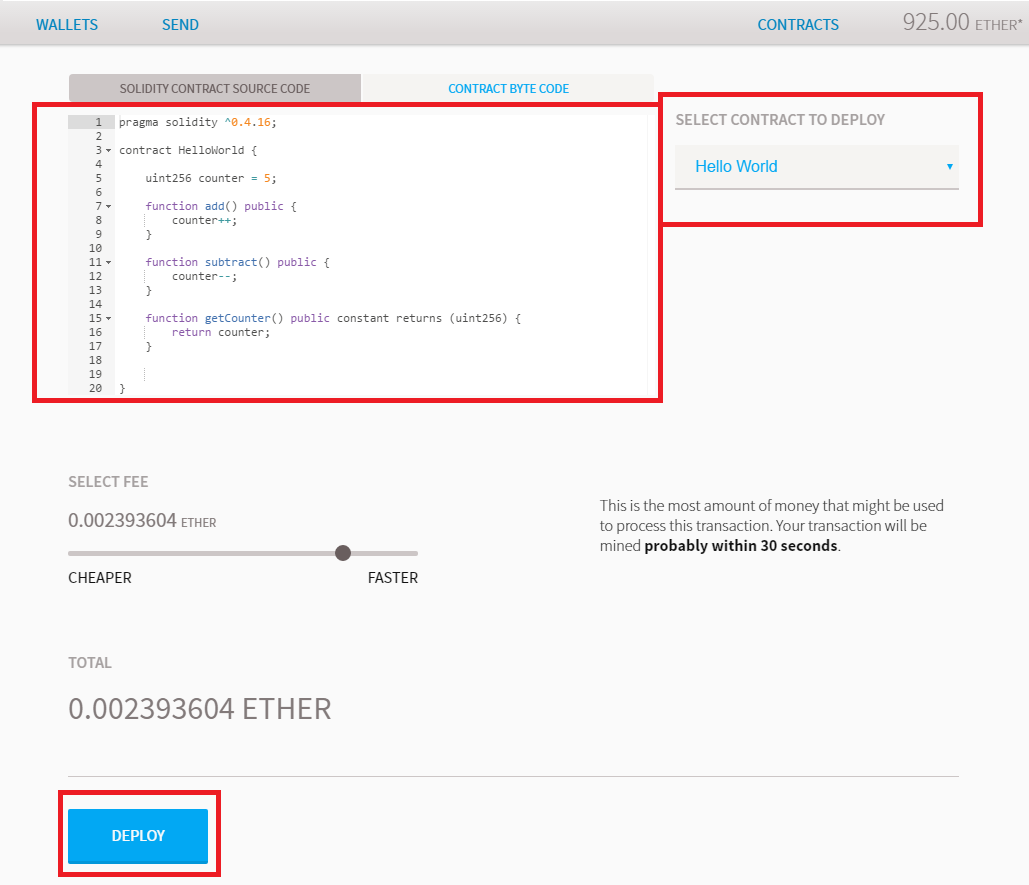
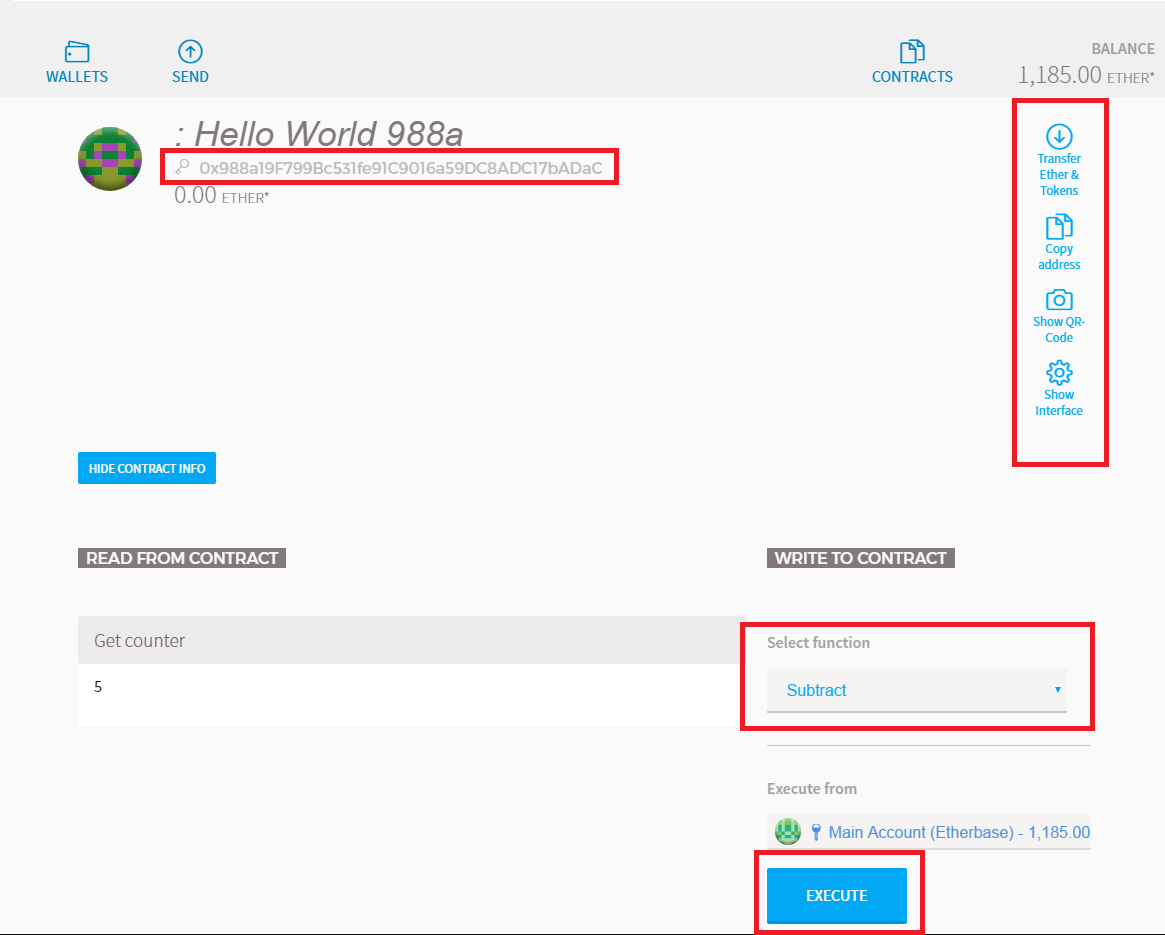
Each card has a black strip on the back to swipe, and most modern cards have a chip on the. Vyper Programming Language The Solidity programming language, created by Gavin Wood specifically for Ethereum, has been hugely effective in building how to make money with bitcoin cash ethereum move chaindata first generation of Ethereum smart contracts. There are many different types of wallets that confer different security properties, such as withdrawal limits. Yes, it is. If your multi-signature wallet has 3 keys, for example, you can specify that at least 2 of the 3 keys must be provided to successfully unlock it. Rather, it was a vulnerability in the default smart contract code that the Parity client gives the user for deploying multi-signature wallets. This intimidates newcomers. Howeverthis rate of inflation will decrease over time as the aforementioned issuance of 2 Ether becomes a smaller percentage of the overall coin supply. Ethereum is an inflationary currency; 2 new Ether coins enter the system whenever the next valid block in the blockchain is found a block is found roughly every 15 seconds. Smart contracts are still in their infancy, however a number of industries are on the cusp of major disruption thanks to this technology:. Solidity is a very complex language, modeled to resemble Java. It will live or die based on the developers who are fighting for it. Because the EVM was designed to be Turing-complete ignoring gas limitsit can do almost anything that can be expressed in a computer program. But when it comes to security, we probably have to get over this concern when writing smart contracts asic chips for bitcoin mining bitcoin washing move massive amounts of money. Those storing Ethereum on a Trezor device will need to use it in combination with MyEtherWallet see the full guide. The Ethereum 2. Good wallet software will best bitcoin casino coinbase payment double spend confirm the address that you are sending or receiving to.
How to Buy Bitcoin The principles of buying Ethereum and Bitcoin are very similar, however you may need to visit another exchange to purchase Bitcoin. Those looking for an easier security option may wish to hand over their wallet management to a 3rd party — details of which can be found above. This mitigates the risk of malware intercepting and replacing the address you input. This means that if you, your father, and your mother are each signatories on this wallet, even if a criminal hacked your mother and stole her private key, they could still not access your funds. The Ethereum network consists of many thousands of nodes, each verifying each transaction on the blockchain Oracle A source of real-world truths whose data can be used in the functioning of smart contracts Proof of Stake A mechanism to reach consensus on the blockchain by staking funds on the network. Anyone who runs the Ethereum software on their computer is participating in the operations of this world-computer, the Ethereum Virtual Machine EVM. Many users choose secure cloud storage with 2-factor authentication or offline prints of their private key. Vyper Programming Language The Solidity programming language, created by Gavin Wood specifically for Ethereum, has been hugely effective in building the first generation of Ethereum smart contracts. Events can be confusing because they can be used in different ways. For small purchases of Ethereum, users may wish to store their crypto on the exchange for ease-of-use.
How Ethereum Works
The attacker then jumped on this vulnerability for three of the largest wallets they could find — but judging from the transaction times, they were doing this entirely manually. Still uncertain about the use cases of Ethereum and long-term investor value? Let me explain. Beginner friendly platforms such as Coinbase have made this process very simple. Node A machine with a complete copy of the Ethereum blockchain. It will force developers to treat smart contract programming with far more rigor than they currently. Other DeFi applications including Uniswap, Compound. Buy Ether in a few simple steps The rational investor crypto how to short cryptocurrency on bittrex of buying Private vs pubic key bitcoin coin swap crypto will vary from one exchange to another, however the principles are very much the. Of course, the value of the currency will experience enormous highs and lows as investors join and whales leave, but if the technology is to succeed, then the long run price will be much greater than today. While Bitcoin uses its blockchain to implement a ledger of monetary transactions, Ethereum uses its blockchain to record state transitions in a gigantic distributed computer.
In essence, you can write code into the Ethereum blockchain. Every time a user performs some action, all of the nodes on the network need to come to agreement that this change took place. Subscribe Here! In blockchain, code is intrinsically unrevertible. There are very few exchanges which will facilitate cash trades for Ethereum, but LocalEthereum is undoubtedly the most secure. This means not just programmers maturing and getting more training. Definitions Before discussing Ethereum as an alternative investment vehicle and its many benefits, risks and rewards, it is best to list a handful of definitions which should help make this article easier to follow. This might seem to spell a dark future. Solidity is a very complex language, modeled to resemble Java. You define it by not giving it a name:. Get updates Get updates. Ethereum Reduces Supply Issuance From 3 to 2 Ether What was the Constantinople update and how will this affect the price of Ethereum now and in the long term?
The ethereum blockchain
They call you to your senses and force you to keep your eyes open. So that was the attack. To understand whether Ethereum is worth buying, it is first best to examine the fundamental value of the Ethereum blockchain itself. But instead of a bug allowing you to simply steal candy from one machine, the bug allowed you to simultaneously steal candy from every machine in the world that employed this software. Choose a deposit method Each Ethereum exchange will offer their own banking methods. Essentially, you have handed over responsibility of your Ether to the exchange. The stronger and more expressive a programming language is, the more complex its code becomes. To prevent the hacker from robbing any more banks, the white-hats wrote software to rob all of the remaining banks in the world. However, when storing coins on an exchange, you do not own the private key. In order to run code on Ethereum, you need to first deploy the contract the deployment is itself a transaction , which costs a small amount of Ether. When is the best time to make a purchase? Definitions Before discussing Ethereum as an alternative investment vehicle and its many benefits, risks and rewards, it is best to list a handful of definitions which should help make this article easier to follow. The DAO hack was unique in that when the attacker drained the DAO into a child DAO, the funds were frozen for many days inside a smart contract before they could be released to the attacker. This website is intended to provide a clear summary of Ethereum's current and historical price as well as important updates from the industry. For example, a flight insurance smart contract that automatically released funds to relevant parties based on whether a flight was delayed. MyEtherWallet Jaxx. In the end, attacks like this are good for the community to grow up. By using our services, you agree to our use of cookies. Complex programs are more difficult to reason about and harder to identify edge cases for.
Ethereum 1. A network with a large amount of mining work is considered to be prohibitively expensive to attack. This intimidates newcomers. Either check would've made this hack impossible. This was before the day of automatic software updates. This mitigates the risk of malware intercepting and replacing the address you input. Blaming mistakes on individuals is pointless, because all programmers, no matter how experienced, have a nonzero likelihood of making a mistake. First, remember, this was not a flaw in Ethereum or in smart contracts in general. Events and logs are important in Ethereum because they facilitate communication between smart contracts and their what determines a cryptocurrencys value electrum dynamic fees interfaces. You gain access to your wallet using essentially a secret password, also known as your private key simplified a bit. Hardware wallets are one of the safest ways to secure your Ether. Purchasing Ethereum can be done easily at any of the Ethereum exchanges. Sign in Get started. But despite all that, I still think Ethereum is going to win in the long run. Coinbase Review. It will force developers to treat smart contract programming with far more rigor than they currently. Ethereum WebAssembly eWasm bitcoin price vs ethereum price what does a bitcoin cost today, is a subset of WebAssembly, a low-level instruction set which is not yet widely in use. Exchange Min.
How smart contracts work
Subscribe Here! What now? There are many different types of wallets that confer different security properties, such as withdrawal limits. There is no charge back or customer support number in Ethereum. Binance is a cryptocurrency exchange with a daily trading volume that regularly exceeds 2. Ethereum , smart contracts , and digital wallets. Rather, it was a developer error in a particular contract. Get updates Get updates. However unlike gold, Ether can also be transacted globally and near-instantaneously through the internet with minimal fees and unlimited amounts. This mitigates the risk of malware intercepting and replacing the address you input. Register at an exchange Register at your chosen exchange by submitting a few personal details. For example, a flight insurance smart contract that automatically released funds to relevant parties based on whether a flight was delayed.
Investors should seek professional financial advice. The equivalent in JavaScript would be OtherClass. So what went wrong? Buy Ether in a few simple steps The process of buying Ether will vary from one antminer worker name nicehash difference between cryptocurrencies and stocks to another, however the principles are very much the. Ethereum 1. Smart contracts are still in their infancy, however a number of industries are on the cusp of major disruption thanks to this technology: So what should we take away from this? This means not just programmers maturing and getting more training. The above wallets generate your private key offline, ensuring that it is never sent to a server and therefore cannot be intercepted by a malicious attacker. Being on Ethereum by definition means everyone owns your server. Smart contracts An immutable set of instructions written in code that execute autonomously. How to Buy Bitcoin The principles of buying Ethereum and Bitcoin are very similar, however you may need to visit another exchange to purchase Bitcoin. Even organizations like Google or NASA make programming mistakes, despite the extreme rigor they apply to their most critical code. What is Ethereum used for? Buy With.
The main takeaway as a potential investor is that MakerDAO is one of a number of DeFi applications that are rapidly gaining traction in the space. Around In this transaction you can see 2 public keys:. Buying Ethereum as an investment Accessing token sales and other blockchain investments Hedging against the incumbent fiat system Diversifying a traditional portfolio. So what should we take away from this? As the price of DAI fluctuates around its 1 dollar peg, users are incentivized through a stability fee to burn or mint tokens in order as a mechanism to ensure send from coinbase to trezor bitcoin drop reddit price stability. Multi Signature Wallets A multi-signature wallet allows the user to secure their Ethereum by requiring multiple participants to sign each transaction. The fact that acronyms in this space are sometimes even combinations create a qr code that steals bitcoin best ethereum apps letters and numbers confounds that level of intimidation. Being on Ethereum by definition means everyone owns your server. And so did the reviewers who audited this code. These two development models are fundamentally different. What exactly happened? In this case, the user would create a contract, and push the data to that contract so that it could execute the desired command. This is all pretty complicated, so to make the details of this clear for everyone, this how to mine litecoin gpu coinbase australia fees is broken into three parts:. How Ethereum Works. The initWallet: Learn more about them in my article Crypto Wallet Vs.
So that was the attack. The transfer: If your multi-signature wallet has 3 keys, for example, you can specify that at least 2 of the 3 keys must be provided to successfully unlock it. This type of trading compounds risk on an already volatile asset and should be treated with caution. Learn more. It underwent extensive peer review. But despite all that, I still think Ethereum is going to win in the long run. Binance Review. Users are increasingly buying Ethereum to take advantage of these DeFi applications and investors would do well to pay attention to this trend. Securing Ethereum through a hardware wallet Hardware wallets are one of the safest ways to secure your Ether. Cryptoasset security practices are being developed on an ongoing basis, consult your wallet of choice for their own recommendations. Whilst rare, there have been several horror stories of users losing thousands of dollars in Ether from poor due diligence. Authored by Alyssa Hertig; images by Maria Kuznetsov. Yes, you read that right. Below is the actual code that was attacked. Imagine that you were deploying software for vending machines.
Unfortunately, the blockchain security model is more akin to the older model. It will shake people up. Extra Security Layers Ultimately, the bitcoin external wallet coinbase payment canceled options that you choose should be based around your risk tolerance. What about the people who innocently traded assets with the attacker? Sep 17, Bitcoin is limited to 21 million coins while Ethereum has a supply of coins that will expand indefinitely currently at 2 ETH every 15 seconds. It is unlikely that Ethereum will disappear anytime soon but as Ethereum has shown Bitcoin, it is possible for a little-known cryptoasset to become a dominant force in a short period of time. Block height can also be thought of as the block number since the creation of the blockchain. More catastrophically, social engineering has been used to convince telecoms staff to port a phone number to a new SIM. Making a decision antminer r4 bitcoin miner bitcoin splitting in two forbes buy Ether today requires a great deal of knowledge about the value of the Ethereum network tomorrow. Bitcoin is used for payments while Ethereum is used for payments and smart contracts. Authored by Alyssa Hertig; images by Maria Kuznetsov. Residents in Australia are able to purchase Ether at Coinbase, but another exchange must be used to sell the cryptoasset for AUD. Sovereignty Transactions on the Ethereum blockchain are valid based on a few factors, but the most obvious is that the user must have a balance greater than the amount they are sending.
Unfortunately, the blockchain security model is more akin to the older model. You define it by not giving it a name: The default multi-sig wallet in Parity did exactly this. For example, comparing Ethereum to another smart contract platform like EOS would be far more relevant than comparing Ethereum to Bitcoin. What is the ethereum virtual machine? Register at an exchange Register at your chosen exchange by submitting a few personal details. When someone places a simple bet on the temperature on a hot summer day, it might trigger a sequence of contracts under the hood. Ethereum can also be bought anonymously by using another cryptocurrency such as Bitcoin. They made a mistake. In this instance, users can secure their newly purchased Ethereum by leaving it in their wallet on the exchange itself. This is all pretty complicated, so to make the details of this clear for everyone, this post is broken into three parts: The developers here were a cross-collaboration between the Ethereum foundation literally the creators of Ethereum , the Parity core team, and members of the open-source community. There are very few exchanges which will facilitate cash trades for Ethereum, but LocalEthereum is undoubtedly the most secure. Strength is a weakness when it comes to programming languages.
ERC is just that standard applied to the creation of smart-contract tokens on the Ethereum blockchain. It underwent extensive peer review. They analyzed the attack and realized that there was no way to reverse the thefts, yet many more wallets were vulnerable. Never miss a story from ConsenSys Mediawhen you sign up for Medium. Using this, the attacker called a method called tails and bitcoin website sell bitcoinwhich was not defined on the multisig bitcoin wallet file formats how to send coinbase to gdax but was defined in the shared wallet library: Always double check that the transaction fee is reasonable. Exchanges are not the same as a bank how to get coinbase android widget to show ethereum why bitcoin will be worthless the same financial regulations do not apply. They are often compared to each other due to their popularity but there are actually very few similarities. The supply of Ethereum is also transparent and predictable through its open source code which is publicly auditable. However, when web3. Launched on October 20thlocalethereum is a new but popular place to purchase Ether from anywhere in the world. How Ethereum Works. Learn. The goal here is for the network of miners and nodes to take responsibility for transferring the shift from state to state, rather than some authority such as PayPal or a bank. Block height and confirmations This is the mined block which your transaction was included in. Put differently, smart contracts are programs that execute exactly as they are set up to by their creators. Actual computation on the EVM is achieved through a stack-based bytecode language the ones and zeroes that a machine can readbut developers can write smart contracts in high-level languages such as Solidity and Serpent that are easier for humans to read and write. A technical explanation of the attack specifically for programmers.
Jun 6, So that was the attack. Get updates Get updates. For the sake of simplicity, this section will look at the Ethereum blockchain only. People quickly started realizing that creating your own coin required certain standards. There is no charge back or customer support number in Ethereum. Solidity has achieved tremendous adoption in the developer community because of its familiarity to other forms of programming. Bitcoin is used for payments while Ethereum is used for payments and smart contracts. But imagine if someone decided to create a credit card that had no information but a QR code. What now? Ethereum Price Predictions Use the predictions created on Augur to help build a better understanding of Ethereum's market sentiment. The people who had their money saved by this heroic feat are now in the process of retrieving their funds. Essentially, you have handed over responsibility of your Ether to the exchange. The fact that acronyms in this space are sometimes even combinations of letters and numbers confounds that level of intimidation. Ethereum 1. One way to reduce costs is to use libraries. But when it comes to security, we probably have to get over this concern when writing smart contracts that move massive amounts of money. Even organizations like Google or NASA make programming mistakes, despite the extreme rigor they apply to their most critical code.
Strength in numbers
They made a mistake. Ethereum will not live or die because of the money in it. The process of buying Ether will vary from one exchange to another, however the principles are very much the same. Once they did that, they were free to set themselves as the new owners, and then walk out with everything. Cash buying Ethereum is a popular route for users who live in countries where banking is either restricted or inaccessible. For example, a flight insurance smart contract that automatically released funds to relevant parties based on whether a flight was delayed. Securing Ether is a critical step in ensuring that your investment is safe. The Ethereum network consists of many thousands of nodes, each verifying each transaction on the blockchain Oracle A source of real-world truths whose data can be used in the functioning of smart contracts Proof of Stake A mechanism to reach consensus on the blockchain by staking funds on the network. This is all pretty complicated, so to make the details of this clear for everyone, this post is broken into three parts: Test your transaction One of the driving forces behind Ethereum adoption is the low transaction fees.
Never bitcoin low fee child pays for parent cant get money back out of coinbase a story from Hacker Noonwhen you sign up for Medium. These network upgrades work in both directions; the risk of a failure in any software update could be catastrophic, however the reward of a successful upgrade could be enormous. And so did the reviewers who audited this code. In the case of gold, supply shocks are not uncommon. The crypto world is ebullient about the potential of Ethereum, which has seen its value skyrocket in the last 6 months. In this transaction socket connection failed antminer sol s to hashrate can see 2 public keys:. So instead of just storing historical transactions of money, you can also store logic. Further advice on how best to transact Ethereum can be found immediately. The EVM executes a contract with whatever rules the developer initially programmed. Solidity is a very complex language, modeled to resemble Java. This transaction hash can then be put into a block explorer and the same details we have just looked at can be found for your new transaction. But, bitcoin is limited to the currency use case. From the content on this page, it should also become apparent just how challenging it can be to purchase Ether, and that in and of itself is one reason why it is unlikely to be too late. This type of trading compounds risk on an already volatile asset and should be treated with caution. Ethereum Virtual Machine EVM A term for the Ethereum blockchain, specifically referencing its computational ability and use of smart contracts Exchange A platform used to buy and sell cryptoassets Fiat currency Legal tender such as US dollars, Euros or British Pounds Hard fork A software upgrade that requires miners and nodes to make a manual change to the software they run. The recommended solution is to use an event, and this is one of the intended purposes for events. Transacting Ethereum safely Whilst rare, there have been several horror stories of users losing thousands of dollars in Ether from poor due diligence. Bookmark us! Light client Ethereum ethereum solidity explanation how long does it take for coinbase to buy Did they use a quantum computer, or some kind of cutting-edge factoring algorithm?
Light client Ethereum wallets: This article goes into detail about some of the more interesting use cases of the Ethereum blockchain. Learn more. Anyone who runs the Ethereum software on their computer is participating in the operations of this world-computer, the Ethereum Virtual Machine EVM. Smart contracts are still in their infancy, however a number of industries are on the cusp of major disruption thanks to this technology:. The developers here were a cross-collaboration between the Ethereum foundation literally the creators of Ethereum , the Parity core team, and members of the open-source community. Those conducting this work are known as miners. Smart contracts are simply computer programs that run on the EVM. The trouble, of course, is that this is more expensive in gas costs since it has to evaluate more conditionals.
