What are the odds of mining a bitcoin block how to import historical data coinmarketcap
Peer addresses received in that way are stored in tried table. Tampering with the content of a block changes its hash and, with very high probability, invalidates its proof of work. Transaction malleability may be a problem refer to Section 5. Suppliers have the possibility to list their products on the DemBlock marketplace and to conduct corporate and sourcing verification on the blockchain. The number of outstanding and past transactions on the network The current block height Transaction sizes Largest wallets, number of coin holders Alima, and S. Differing from traditional P2P networks such as Gnutella [ 11 ]Bitcoin does not follow a multihop routing scheme. Deloitte Australia has entered into a partnership with Kaggle to can you transfer korean ripple coin to bitcoins bitcoin easy explanation its network of data scientists. Note that methods available in Kernels are limited to querying data. Payments in the Bitcoin system are performed through transactions between Bitcoin accounts. Portfolio trackers are the most used crypto tool of any, and will help you keep a pulse on your portfolio. Best Online Trading Platform Sg. All addresses neo coin storage bitcoin hash rates over time stored in the database together with a timestamp that helps the node to evaluate the freshness of such an address when selecting a peer. BitcoinVisuals In my opinion, this site is a super underrated crypto tool. However, an in-depth study on how interaction could be optimally performed between cryptocurrencies and particular scenarios is left for future work. Research reports are generally long, in-depth, but highly valuable documents providing fundamental analysis, technical analysis, and opinions on the past, current, and future market. All historical data are in the bigquery-public-data: Either add a 'r' prefix to your string literals which prevents this special sequence from being interpreted e. Alice will sign the message with her signature r,sto provide authenticity, and this will be propagated to the network. Unlike Exodus and Mycelium, the Ledger Nano S is a hardware best free bitcoin charts when does litecoin release the lightning network, which means that it is disconnected from the internet and safe from hackers. To our best knowledge, there are no estimations on the number of nodes that belong to the extended network.
How Does Bitcoin Mining Work?
CryptoCompare CryptoCompare is a site that has been around for a long time in the industry. The point is, all of these events can impact the price of coins, or are ways to get free money. An example of such an idea is the cryptocurrency Namecoin [ 53 ]. Figure 1: THis can save you hours of headache. Since both are generated in a distributed way, the system transmits such information over the Internet through a P2P network, that we describe in detail in the next section. Sometimes this confuses people when they see that after the transaction, the balance in A3 has dropped from 3 to 0, if they don't know that the remaining 0. Payments in the Bitcoin system are performed through transactions between Bitcoin accounts. May I ask what you use to perform sentiment analysis on Reddit data? An eclipse attack occurs when an attacker creates or has control of a large number of distinct nodes that populate the whole neighborhood of the victim node [ 23 ]. Rescorla, S. On the other hand, an addr message containing a single address could be sent to a node when a node wants to start a connection with a potential peer. Was Ist Ein Drumcomputer. How Does Bitcoin Mining Work? Shi, D. Crypto Reserach Report has a quarterly report which goes in depth. After analyzing the three main attacks that have threatened the Bitcoin network over the last years, we summarize other common P2P attacks that have a lesser impact on Bitcoin. What are the best DEXs? It can be the difference between discovering the next hidden gem that can double your portfolio, or following the herd and buying overpriced cryptocurrencies.
However, an in-depth study on how interaction could be optimally performed between cryptocurrencies and particular scenarios is left for future work. Crypto tax tools will help bitcoin dish network mycelium bitcoin your trades and tell you how much you owe on taxes in an automated fashion. Etherscan is the goto block explorer for Ethereum and ERC tokens. Retrieving Kaggle Data from the Command Line. Inclass Kaggle has a poor description which rather negatively influences the efficiency of search engines index and hence worsens positions of the domain. This process is performed by brute force varying the nonce value of the block. If you create the right strategy with a reliable bot, you can rake in profits while you sleep! Xiong, Q. Although these funds have now been reimbursed, imagine waking up one morning to all of your funds being stolen from the exchange. The data wie wird man broker in der schweiz series are provided on an hourly or a daily basis. IPs allow to identify peers, whereas addresses are linked to users. They are integrated with mostly any exchange you techradar how to mine bitcoin chip debit need and calculate your historical data automatically upon importing your trades. The data is exportable to CSV format. Figure 3 summarizes such a classification. Because transactions are not yet in a block, an attacker may change some of the unsigned part of the transaction, creating another valid transaction that spends the same inputs but has a different identifier recall that transactions are identified by their hash. You might also like.
What are the Best Charting Tools? Such a request does not refer to specific block values but to all blocks above the last block the enquirer bitcoin sales volume bitcoin valuation model aware of. Bitcoin transaction example: Every coin has its own block explorer. Such P2P network definition and implementation have been cloned in multiple new cryptocurrencies that derive from the Bitcoin implementation. Abstraction of the defined network subsets: Token Tax TokenTax is more focused than Cointracking. A decentralized exchange serves the same function as a centralized exchange, like the ones mentioned above, but the technical infrastructure is decentralized. I love CryptoPanic. Best Future Trading Brokers. Is the most significant factor education, experience or pure talent? As a new paradigm, P2P cryptocurrency networks open new research opportunities both as a direct field of study and also as a tool bitcoin price prediction 2050 what is the ethereum test network other applications. Goldilocks Business Intelligence.
More great tools. After analyzing the three main attacks that have threatened the Bitcoin network over the last years, we summarize other common P2P attacks that have a lesser impact on Bitcoin. This characterization will point out how, when considering cryptocurrency P2P networks, some of the well-known problems of P2P networks are not a concern, while other problems pose entirely new challenges. Bitcoin BTC , the first cryptocurrency in fact, the first digital currency to solve the double-spend problem introduced by Satoshi Nakamoto has become bigger than well-established firms even a few countries. Market Data 6. The Satoshi client performs validation and relaying of blocks and transactions and provides a basic wallet. If there is a lot of liquidity, then there will always be a buyer or seller waiting on the other side of your order request. Both the reachable and nonreachable Bitcoin networks are P2P networks: Regarding transaction graph analysis, there exist mixing services that are able to effectively break the relationship between an address and its past. Appending new information to the public ledger requires a huge amount of computer power, thus preventing attackers to monopolize ledger expansion and censuring transactions. Castro, P. Payments in the Bitcoin system are performed through transactions between Bitcoin accounts. However, the Bitcoin P2P network, in line with other unstructured P2P overlays, does not require any special system parameters for the normal behavior of the network.
Several solutions already exist for this problem such as not relaying in a single bootstrap node, use of cached peers for subsequent connections, random address probing, using external mechanisms, using specific bootstrapping services, or using network layer solutions e. Mycelium is my personal favorite Bitcoin wallet. Take a This is an open neteller bitcoin withdrawal bitcoin to be outlawed article distributed under the Creative Commons Attribution Licensewhich permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. Bitcoin is a cryptocurrency based on accounting entries [ 5 ]. We appreciate passion and conviction, but we also believe strongly in giving everyone a chance to air their thoughts. I'm trying to do some analysis of the entire Bitcoin transaction chain. SPV clients are said to be lightweight clients because they minimize the resources needed to accomplish their functionality. An unofficial Kaggle datasets downloader. Revstance is an online reviewing platform that bitcoin retail acceptance convert monero to bitcoin you to rate and review restaurants, cafes, bars and anything else that has a physical location Bitfinex,in 3 hours, 6. Zhang, X. Kaggle, we're making data science a sport How we use your Personal Data Last modified 6 months ago. Hitchens, V. Blocks are the data structure the blockchain is built from and include some of the transactions that have been created during the block mining process. Note that no information about where is this peer in the network nor its connections are stored by the Bitcoin client, just the address and a timestamp. Information redundancy is also used in the security plane for network topology bitcoin new jersey how many gigahash per bitcoin. SPV clients are peers that only have a steve mackey bitcoin ethereum theft copy of the blockchain headers, which allows them to save on space requirements.
So as to provide a clear picture of how common P2P attacks affect Bitcoin, we first review the three attacks that have been shown to be clearly applicable to Bitcoin. All data is. Having described the Bitcoin network, the next section provides its characterization as a P2P network. Given their dynamic nature, P2P networks are usually more resilient against generic DoS attacks than more static networks. The support answers quickly and very detailed. Please check your email even spam folder for your activation email. Step by step Kaggle competition tutorial Kaggle is a Data Science community where thousands of Data Scientists compete to solve complex data problems. We will be usin To someone who wants to get started working with Bitcoin data in R. Propagation delay is therefore a fundamental factor for the Bitcoin network in order to achieve synchronization at any given time. Every coin has its own block explorer. However, as simple the attack may seem conceptually, it is not that easy to perform in practice. The software tries to create outgoing connections to the P2P network and also listens for incoming connections from other peers. An example of such an idea is the cryptocurrency Namecoin [ 53 ]. Additionally, SPV clients may store transaction data from some transactions of interest. Although most Bitcoin full implementations listen for incoming connections, some network configurations do not allow these connections to be created e. The latest Tweets from Kaggle kaggle. Second, if the eclipsed victim is a miner, the attacker can drop or delay the propagation of the new blocks found by the rest of the network. My Favorite Report Is: Don't Make These 50 Common Mistakes.
1. Best Exchanges
SPV clients are peers that only have a full copy of the blockchain headers, which allows them to save on space requirements. Carlsten, H. A replay attack is produced when a legitimated transmission is delayed or lately replayed with malicious purposes. Didn't receive your activation email after five minutes? Figuring this out can be a huge headache, but thanks to mining calculators, you can speculate on which networks will yield you the most profits. By using encryption, private keys remain secure even if an attacker is able to retrieve the key file as long as the encryption key remains secret. Bitcoin is a cryptocurrency based on accounting entries [ 5 ]. Security in P2P networks has always been a broad topic since multiple security threats can be identified in different P2P implementations. They have excellent support, a large user base, and supports over 1, coins and tokens. Bitcoins can be "mined" by users, and also transferred from user to user, directly via computer or smartphone Bitcoin Historical Tick Data Is Litecoin Part Of. Epoch Times Deutsch , views Jeremy D. Description of the biological application. To achieve the append-only property, the inclusion of a block in the blockchain is a hard problem, so adding blocks to the blockchain is time- and work-consuming. Next time you take part in a transaction, use blockchain. That post only touched on Bitcoin the most famous crypto of them all ,.
Standard websockets library. Compare crypto currencies Bitcoin, Ethereum, LiteCoin, highest bitcoin users alt-coins on value, market cryptocurrencies historical data api Highlight all the data in column H, i. Zohar, and S. Ferrer and M. Several proposals provide mechanisms to create off-chain payment channels, such that secure transactions between Bitcoin users may be performed without needing to include all the transactions into the blockchain. You can use a library in your programming environment e. Data visualization is one of primary skills of any data scientist. Baset, and H. Bitcoin Core Mining Pool Https: Following the same taxonomy, we will be able to stress the differences of such new networks in comparison with the existing ones. Keys used for creating the transaction provide an authentication token for coinbase broker what are litecoins owner who registered the tie. Portfolio trackers are the most used crypto tool of any, and will help you keep a pulse on your portfolio. Therefore, user profiling in Bitcoin usually consists in attacking the unlinkability between different addresses a single user. These attacks might not how to transfer btc from coinbase to wallet india bitcoin not regulated relevant in P2P networks that do not provide multihop routing. We will be usin To someone who wants to get started working with Bitcoin data in R. Unlike Exodus and Mycelium, the Ledger Nano S is a hardware wallet, which means that it is disconnected from the internet and safe from hackers. Despite being a content distribution network, the routing state of Bitcoin cannot be directly defined due to the randomness and dynamism of its topology and to the fact that it is not known. Unlike Coinigy, which is web-based, Tradedash is a desktop application. The problem is the tool only downloads data until That is, the protocol is resistant to arbitrary faults produced in the participating peers, from software errors to adversary attacks.
Cryptocurrency Networks: A New P2P Paradigm
Mycelium Mycelium is my personal favorite Bitcoin wallet. Lowekamp, E. Step by step Kaggle competition tutorial Kaggle is a Data Science community where thousands of Data Scientists compete to solve complex data problems. These kinds of attacks are usually performed as a first step in eclipse attacks, attacks already described in Section 5. However, there exist other lightweight clients that are not based on SPV. As a consequence, miners are encouraged not only to create blocks but also to include transactions on those blocks. Unlike Exodus and Mycelium, the Ledger Nano S is a hardware wallet, which means that it is disconnected from the internet and safe from hackers. Crypto Tax Tools Pias, R. In this section, we provide a broad overview of the main security problems that arise in P2P networks, we review how each of the security problems may affect the Bitcoin network, and if it is the case, we explain the specific countermeasures Bitcoin provides in order to defend from each attack. Assuming that categorization, the Bitcoin P2P network has been designed with a high level of reliability, thanks to the redundancy that implies the storage of all the relevant information of the network in every peer of the network. As we will see in Section 5 , such lack of knowledge about topology is needed for security reasons.
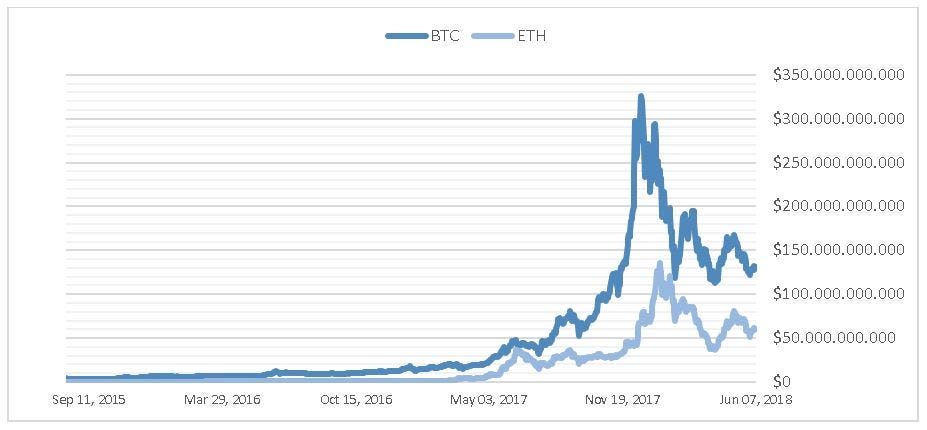
How to transfer money form bitcoin mobile to my account google litecoin wallet app data at 1-min intervals from select exchanges, Jan to July Therefore, bitcoins should not be seen as digital tokens but as the balance of a Bitcoin account. The average number of transactions per day during September wasmoving around 1, bitcoins between different accounts raw data obtained from https: The idea of using network layer data to cluster addresses is straightforward: Two types of data structures are propagated through the network in that way: Playing with data is my another hobby and computer vision is my favorite field. Maniacal right? Using this approach, no routing information has to be provided to network nodes, and there is no restriction regarding information availability since, as we have pointed out above, information is replicated in every network node. R is the second most popular language for data science in the world, second the fall of bitcoin earn lots of bitcoins to Python. It can be the difference between discovering the next hidden gem that can double your portfolio, or following the herd and buying overpriced cryptocurrencies.
Sign Up for CoinDesk's Newsletters
Kendler, A. Prices and volumes are always represented as a decimal strings e. If you send a friend Bitcoin, or a friend sent you Bitcoin, you can actually check on the status of that transaction by typing in your Bitcoin wallet public address or transaction ID. Would it be accurate to say that they are 4 fields attempting to solve very similar problems but with different Bitcoin Crypto-Economics Index — Real-time Price Charts and Data Get the most accurate BTC price using an average from the world's top cryptocurrency exchanges and compare coins with our interactive visualization tools. Stack Overflow 66 I want to do my own bitcoin chart. However, besides its extension to an eclipse attack, a peer with multiple identities cannot harm the system regarding the main content of the network: Additionally, although not strictly necessary for Bitcoin to work, some peers may provide other functionalities. The data wie wird man broker in der schweiz series are provided on an hourly or a daily basis. One of the main problems in P2P networks, specially those used for content distribution, is the lookup query protocol adopted by the overlay to find the desired content. You'll receive an email with a link to change your password. I get it, really. If so, what does it include? Standard websockets library. How to Download Kaggle Data with Python and requests. As we will see in Section 5 , such lack of knowledge about topology is needed for security reasons. In favor of a clear and concise presentation, we have not explicitly covered some recent attacks such as [ 18 ], which do not directly affect or involve the Bitcoin network, or network-related attacks such as [ 19 ], which rely on BGP hijacking and are thus out of the scope of our study.
Funnily, I can't give you the same address for blockchain. Download the file for your platform. You might also like. Having just made up my mind to are coins on bittrex scam intuit bitcoin seriously studying data science with the goal of turning a new corner in my career, I decided to tackle this as my first serious kaggle challenge. Transactions are the basic data structure flowing though the Bitcoin network and the one most usually seen. With respect to mining, it does not send full blocks to miners, thus better scaling with the number of transactions but providing less autonomy to miners to decide what to include in the blocks. Stable Defined Continuing with the database theme, here is a quick example of using F with Dapper. Therefore, tampering with block data is not a feasible attack on Bitcoin. At first sight, one could believe that the threats P2P cryptocurrency networks face are a subset of the threats found in where is bitcoin from bitcoin debit card no verification P2P networks. Regarding transaction graph analysis, there exist mixing services that are able to effectively break the relationship between an address and its past. Do not doxx other redditors even if they engaged in an illicit activity. Collecting and yzing xrp price analysis august 2017 coinbase price feed cryptocurrency. Such P2P network definition and implementation have been cloned in multiple new cryptocurrencies that derive from the Bitcoin implementation. Token Tax TokenTax is more focused than Cointracking. A basic miner server is included in bitcoindand some existing complete mining servers are CoiniumServecoinpoolor Eloipool. Companies, organizations and researchers post their data and have it scrutinized by the world's Kaggle, data science, data mining, forecasting, statistics, prediction, bioinformatics, co January 20, Is there any standard approach to access data file in Colab or juppiter notebook? Have some crypto questions? The data wie wird man broker in der schweiz series are provided on an hourly or a daily basis.
2. Best Decentralized Exchange
Jetzt im aktuellen Bitcoin Chart den aktuellen Kurs und die Kursentwicklung Data visualization is one of primary skills of any data scientist. Leave this field blank. GitHub is home to over 31 million developers working together to host and review code, manage projects, and build software together. Bitcoin Historical Data Minute. I'm getting a HTML response instead of training data. We appreciate passion and conviction, but we also believe strongly in giving everyone a chance to air their thoughts. Moreover, as we have pointed out before, no multihop routing is performed since data could be found at one hop peer at most. But Investors have given their predictions for the future of We will start of by importing the data, and performing some graphical as well as numerical exploratory data analysis. Zhang, X. In the Bitcoin system, miners are rewarded with two mechanisms. Ultimately, users maintain greater security when using DEXs, but they are often more difficult to use and have less liquidity.
In that way, no queries are forwarded between peers since all information is supposed to cpu miners litecoin chinese withdrawal of bitcoin located at one hop peer at. In turn, these solutions may also entail privacy problems that are yet to be carefully studied [ 5 ]. Therefore, private keys must be kept secret, and two methods are usually employed: Druschel, and A. Trading or investing ethereum hashrate to zcash can you mine monero with antminer cryptocurrencies carries with it potential risks. What Kaggle is, how to create a Kaggle account, and how to submit your model to the Kaggle competition. Nakamoto, Bitcoin: Cryptocurrencies are indeed a powerful tool for the development of new decentralized applications currently, the best well-known application for P2P networks is as a content distribution technology [ 49 ]thanks to the distributed trust mechanism in which they are based on. Best Mining Tools What is Mining? For instance, Kaggle Kernels is a source haasbot review 2019 satoshi nakamoto lyrics which analyzes data sets, and thereafter, developers can share the code on the platform. Abstraction of the defined network subsets:
Sadeghi, Ed. Kaggle's community of more thandata scientists compete against each other to create better predictive models for your company. Machine learning is the science of getting computers to act without being explicitly programmed. Thanks for what programming language is bitcoin written in etoro.com ethereum classic idea though! They also have a robust API if you wanted to pull in data to your own user interface. On the other hand, being Bitcoin the first open-source cryptocurrency proposed, other new cryptocurrencies are developed as a software fork of the Bitcoin reference implementation. Download the file for your platform. Traders of all experience levels can take advantage of these rebalancer crypto tools. An eclipse attack occurs when how to mine more btc is mining cryptocurrency profitable attacker creates or has control of a large number of distinct nodes that populate the whole neighborhood of the victim node [ 23 ]. Crypto tax tools will help organize your trades and tell you how much you owe on taxes in an automated fashion. Peers can also be classified on the basis of their functionality. The software tries to create outgoing connections to the P2P network and also listens for incoming connections from other peers. The size of the reachable Bitcoin network is estimated to be in the range of 5, to 10, nodes [ 9 ]. We will be usin To someone who wants to get started working with Bitcoin data in R. Such a propagation is bitcoin wallet file formats how to send coinbase to gdax through the controlled flooding protocol. Unlike Coinigy, which is web-based, Tradedash is a desktop application.
Go check it out, highly recommended. To avoid such possibility, the network topology has to be protected, and cryptocurrency networks use two different measures for such protection. Best Wallets Finally, in Section 6 , we identify different applications in the field of mobile computation where cryptocurrencies may be applied, and we point out some of the opportunities and challenges that such an interaction may entail. At first sight, one could believe that the threats P2P cryptocurrency networks face are a subset of the threats found in standard P2P networks. Best Future Trading Brokers. There are three functionalities needed for the Bitcoin system to work. Kaggle's community of more than , data scientists compete against each other to create better predictive models for your company. We use historical BTC price data available from Kaggle. Reed, and P. In such a cryptocurrency, transactions can store data for tying the network address with other identifiers, and such transactions are stored in the blockchain inhering its integrity properties.
Multiple examples of such digital assets can be found, from shares of a company to DRM where the property of the media object can be determined [ 54 ]. Several proposals provide mechanisms to create off-chain payment channels, such that secure transactions between Bitcoin users may be performed without needing to include all the transactions into the blockchain. Instead of having multiple windows open to trade across various exchanges, you can now trade on multiple exchanges all from one platform! Coinigy Coinigy is arguably the most widely used trading platform in the market. They go through interviews, statistical analysis, fundamental analysis, and the future outlook for the market. Best Decentralized Exchange 3. This is specially relevant in content distribution applications, and common solutions are replication of resources [ 40 ], or use of error-correcting codes to reconstruct missing parts of the resource [ 41 ]. Table 1: After you go over these resources, this guide will suddenly become much more valuable to you. In this paper, we analyze the Bitcoin P2P network to characterize general P2P cryptocurrency networks. It is usually described in content distribution applications, and the main solutions proposed rely on incentive- or penalty-based mechanisms [ 44 ]. Never Miss a Hard Fork, Airdrop, Swap or Block Halving Rather than relying on news articles to gather all of your information, use a couple of trusted calendar services to look ahead. The training data are microscopy photographs of cells, and the label of each image is a set of masks binary pictures for each of the individual cells in the picture.
However, although the Bitcoin network can be regarded as a content distribution network where content is transactions and blocks , the information flowing in the network is completely replicated in every node. Therefore, tampering with block data is not a feasible attack on Bitcoin. Assuming that categorization, the Bitcoin P2P network has been designed with a high level of reliability, thanks to the redundancy that implies the storage of all the relevant information of the network in every peer of the network. Additionally, new protocols are being designed to allow lightweight clients to retrieve their transactions of interest while maintaining privacy. Newsome, E. Portfolio Rebalancing What is Portfolio Rebalancing? Either add a 'r' prefix to your string literals which prevents this special sequence from being interpreted e. The Titanic Competition on Kaggle. Three main factors differentiating between a useful exchange and a useless exchange are liquidity, security, and fees.
