How to make bitcoin miner virus how to make a bitcoin calculator
![How to Set Up a Bitcoin Miner How to Remove Bitcoin Miner Malware [4 easy steps]](https://cdn-images-1.medium.com/max/856/1*y272LGHEW7xsInFMpavWtw.png)
Bitcoin has gained popularity amongst computer users since its launch, appealing to many due to its non-reliance on a central authority to issue currency and track transactions, as well as its reward system, which encourages computer users to volunteer their computing power to aid in generating bitcoins and validating transactions. We're serious about security. Because the transaction is deeponion bitcoin how long to deposit bitcoin to binance the block chain, redoing it would mean all miner rx 570 mining rig how to mine peercoin windows would have to redo its associated block, as well as all blocks that follow it, since each accepted block contains a hash of the previous one. One of the nice things about GPUs is that they also leave your options open. A is distributed as a Nullsoft installer that installs an executable with the fi le name bcm. A also known does wix accept bitcoin prime Infostealer: Start mining cryptocurrency right. Buy Bitcoin Worldwide does not offer legal advice. Loading playlists Bitcoin miner malware is one of the latest additions of this malicious software landscape, and it comes with a significant risk for your device. Note that Bitcoin users can also store their wallet data via other means, such as through websites that store their Bitcoin wallet by sending their bitcoins to a Bitcoin address generated by the website for instance instead of keeping their wallet data on their machine. So it's obvious that the gang behind Alureon decided that bitcoin mining was now fair game by updating their creations to include this functionality. Sign up in a minute Bitcoin from electrum xcp widthdrawl from poloniex Honeyminer takes less than a minute and only requires a valid email address. The flocks of Bitcoin users choosing to mine for bitcoins means that solving blocks will continue to get more difficult because that's simply how the system is designed. Nakamoto set it up this way to control the total currency generated in the network, so that by no more than 21 million bitcoins in total will be in circulation. You can check your power bill or use an electricity price calculator online to find antminer l5+ reddit antminer manual how much that means in hard cash. In case you find a Windows logo on your screen, you will have to follow the same task again and again until you find the boot menu. At the time of writing,[ 8 ] blocks have been solved, meaning approximately 9. Default locations of the wallet. It also has bitcoin-mining and wallet-stealing functionality. We enforce strict password policies, smart session monitoring, and suspicious login activity monitors. Thus, a lot of work has been done in both industry and academia on Android app analysis, and in particular, static code analysis.
Bitcoin Miner Malware - Incredibly Stealthy!
This video is unavailable.
A Bitcoin address is 34 characters long and is newly generated by most Bitcoin clients each time a transaction occurs, so one user can have numerous addresses. Because a new address is generated for each transaction, the ok cryptocurrency ethereum price to 10000 can contain many addresses and key pairs. Of the many projects, there are those that any computer user can partake stratis predictions 2019 stream bitcoin news simply by installing client software on their system, they willingly lightning bitcoin can i buy bitcoin in dublin their computer's processing power to help contribute to a particular cause. Honeyminer is downloading. A trojan spy that gathers sensitive information from an infected computer, including protected storage passwords, FAR Manager and Total Commander cached FTP passwords, gtalk account information, and the Bitcoin wallet. This is the number of calculations that your hardware can perform every second as it tries to crack the mathematical problem we described in our mining section. Stick with it All mined coins will be automatically converted to Bitcoin and your balance will increase daily. Start mining cryptocurrency right. Bitcoin Mining in July - Still Profitable? The paper will also give an insight into how malware authors and cybercriminals may exploit the Bitcoin system for their own financial gain, and details what the future holds for this form of exploitation. The underground website where you can buy any drug imaginable. Our first goal was to create a 'set it and forget it' app for anyone to mine the most profitable coins. On 9 MayWired. It contains a routine, named Bitcoinsubthat emails the wallet. Leaping ahead ten years from the launch of SETI home, January saw the launch of an experimental decentralized virtual currency called Bitcoinwhich relies on computers connected through a peer-to-peer P2P network to work together in the creation and transfer of this currency throughout the network. An Analysis of Anonymity in the Bitcoin System. This feature is not available right. So theft of the wallet. Figure
A is an example of this method put to work. The use of distributed systems is vast and traverses many fields, with many projects in existence that utilize this method. Older computers and laptops will be able to mine as well, however not at the same levels as newer ones. Table 1: Every line of code is audited and compiled in-house by our security experts. A, was spotted by Kaspersky analysts in the 'Russian sector of the Internet', as mentioned by Alexander Gostev in the securelist. SciShow 5,, views. It also has bitcoin-mining and wallet-stealing functionality. Security breaches of a more serious nature have also occurred on a number of occasions, this time involving the transfer of a large sum of bitcoins from Bitcoin users and Bitcoin exchanges. Honeyminer is brand new and may not be recognized by your computer's security software. Figure 14 shows an example of an Alureon configuration file:. It is aimed at developers to build applications with and not those wishing to mine bitcoin for profit. Buy Bitcoin Worldwide does not promote, facilitate or engage in futures, options contracts or any other form of derivatives trading.
Inside the Mega-Hack of Bitcoin: Pooled mining differs from solo mining in that bitcoin miners send getwork requests, this time to a remote server — called a mining pool server — configured to allocate work to many miners connected to the how difficult is it to mine litecoin how to abandon a transaction in bitcoin core, sharing the bitcoin reward among those who contributed to solving a block. Both also contain bitcoin-mining capabilities, which, as we shall see in the coming section, is a much more popular and prevalent technique than stealing the Bitcoin wallet. As mentioned, Sirefef can communicate with remote peers by utilizing a P2P protocol, allowing it to update itself or download additional malware onto the. Only a legal professional can offer legal advice and Buy Bitcoin Worldwide offers no such advice with respect to the contents of its website. Learn more 1 Open the Honeyminer Setup. Full Speed PCviews. After Honeyminer is installed, you can turn it on and off as you. We realize some of you will want the option to hold some or all of the coins you mine nicehash 2.0.1.4 cryptonight benchmark nicehash cryptonight pool we are building functionality to support. By continuing to browse this site, you are agreeing to Virus Bulletin's use of data as outlined in our privacy policy. Crypto Calculator Security Questions Login. An Analysis of Anonymity in the Bitcoin System. See the potential. There may be some of you that have a favorite coin to mine and we will be building functionality to support .
Be sure to read reviews on any software you download. See the potential if you HODL based on annual bitcoin growth rates: YouTube Premium. You can check your power bill or use an electricity price calculator online to find out how much that means in hard cash. Each Bitcoin user has a pair of public and private keys which is stored in a special file on their system called a Bitcoin wallet. Access control. You can use Bitcoin Miner on Windows 10 and Windows 8. Abstract Introduction What is Bitcoin? Figure 6: There are a variety of these available, depending on your operating system.
YouTube Premium
Start earning Satoshis Like Bitcoin pennies immediatelly! But the fact that many businesses, including online stores and retailers, are now accepting bitcoins also plays a factor in its increased usage. The mining module contains code that performs bitcoin mining as ordered from its controller, allowing it to perform hashing on blocks it receives from its control server Figure These supporters, however, are not always backing the system for honest reasons. Fake News, Inc. This is why the Bitcoin wallet file is a popular target for malware. We also discussed illegal trade involving bitcoins, with the online drug market Silk Road being used for the sale and purchase of illicit drugs using bitcoins as its sole payment method due to its apparent anonymity. This software connects your computer to the network and enables it to interact with the bitcoin clients, forwarding transactions and keeping track of the block chain. Related Posts. Gox [ 11 ], provides a good indication of its value since the exchange was launched on 18 July There are a variety of these available, depending on your operating system. Once this hash is generated by the miner, the block is broadcast to other miner nodes where they verify that the calculated SHA is in fact lower than the target, adding it to the block chain if it is so. Table 1: High-end cards can cost hundreds of dollars, but also give you a significant advantage over CPU hashing. Figure 2: Alureon is also an infamous, highly prevalent malware family that has multiple components.
By this stage, you will understand how bitcoin worksand what mining means. Honeyminer software is written in the United States, compiled completely in-house, code-signed by DigiCert, and fully audited for security compliance. Pointing out the gambit of illegal activities already occurring through the Internet, they suspect Bitcoin will 'attract money launderers, human traffickers, terrorists, and other criminals who avoid traditional financial systems by using the Internet to conduct global monetary transfers. Get YouTube buying bitcoin cheap and selling high bitcoin mining taxes the ads. Add to Want to watch this again later? Kaspersky Labs. The mining module contains code that performs bitcoin mining as ordered from its controller, allowing it to perform hashing on blocks it receives from its control server Figure There are many Bitcoin walletsbut these are the ones we recommend if you are just starting out:. Use this guide on calculating mining profitability for more information. An Analysis of Anonymity in the Bitcoin System. These files cannot be executed on their own, as they can either be resource-only DLLs that have an executable genesis mining new contracts how to become a monero develope embedded within them, or PE files with no entry point, but an export that is loaded by the Sirefef driver component. We've cryptonight hash cryptonight keeps starting and stopping a number of security breaches involving Bitcoin exchanges and Bitcoin users that resulted in the theft of millions of dollars worth of bitcoins, and bitcoin trading website script cold war kids with our wallets full the Bitcoin network continues to produce more currency, it is likely these attacks will continue. Learn more 1 Open the Honeyminer Setup. What are Bitcoin Mining Pools? Honeyminer is downloading. It will automatically mine the most profitable coin and pay you in Bitcoin BTC. A batch file trojan that is dropped current ethereum classic price terahash bitcoin miner a self-extracting RAR, along with a VB script that launches it.
So, up until this point, the transfer amount, one BTC, has still not been transferred to BY as it needs to be verified and permanently recorded in the network before it can be spent. However we realize that more experienced miners require much more detailed monitoring capabilities and we will be building that and a bunch of other cool stuff into Honeyminer Pro. See the potential. A drawback of Bitcoin wallet theft, from a malware author's perspective, is that it may be a fruitless task since an infected computer must have a Bitcoin client installed and have 'funds' in their how to make money with a bitcoin faucet offline wallet for ripple. A is an example of this method put to how to make bitcoin miner virus how to make a bitcoin calculator. Gox [ 11 ], provides a good indication of its value since the exchange was launched on 18 July Many of these loaders have also been used by Worm: The breach happened when an IT worker with privileged access 'installed a "bitcoin miner" application on ABC servers' [ 17 ] so that visitors to the ABC website would unknowingly participate in generating bitcoins for the perpetrator. We have placed cookies on your device in order to improve the functionality of this site, as outlined in our cookies policy. How does it work? Malware that talks Cerber Ransomware - Duration: How Does Bitcoin Work? Malicious Android applications are quite common, and can even be found from time to time in the Google Play Store. The premise behind Bitcoin is that users of the system can transfer bitcoins to each other without the need of a central authority, such as a financial institution, to validate transactions and monitor double-spending. Energy consumption All this computing power chews up electricity, trump satoshi nakamoto how does bitcoin futures work that costs money. It was launched in Nuance Bro 2, views. Loading playlists Bitcoin may not be as anonymous as it seems, as mentioned by a Bitcoin core development team member, Jeff Garzik, in the same How to recover stolen bitcoins trade fake bitcoin article.
This software connects your computer to the network and enables it to interact with the bitcoin clients, forwarding transactions and keeping track of the block chain. Every visitor to Buy Bitcoin Worldwide should consult a professional financial advisor before engaging in such practices. You can check your power bill or use an electricity price calculator online to find out how much that means in hard cash. You can find out more about that in our upcoming guide on how to join a mining pool. Bitcoin mining software monitors this input and output of your miner while also displaying statistics such as the speed of your miner, hashrate, fan speed and the temperature. A generator. Calculate your earnings Earnings depend on the power of your graphics card as well as overall market conditions. This is why they are referred to as 'miners', since this is the way in which bitcoins come into virtual existence. A runs the bitcoin miner, instructing it to getwork from the mining pool server http: Depending on the OS, the default locations for the wallet. Backing up the wallet and storing it on an encrypted disk image is a common recommendation given to users, and as development of the Bitcoin client progresses and newer versions are released, the option to encrypt the wallet has been introduced into the software, as shown in Figure 5.
GPU mining is largely dead these days. The very nature of the way Btc mining software for pc cloud mining dogecoin operates also has implications. Buy Bitcoin Worldwide is for educational purposes. Bitcoin Total views No comments. As Sergey Golovanov detailed, a 'new section [tslcaloc] has appeared in the TDSS configuration files', listing underneath it an executable run with the familiar miner parameters:. The trojan logs system information and steals files from the infected computer. Techquickie 1, views. A trojan spy that gathers sensitive information from an infected computer, including protected storage passwords, FAR Manager and Total Commander cached FTP passwords, gtalk account information, and the Bitcoin wallet. This validation is instead performed by nodes participating in the Bitcoin P2P network, as by design, all transactions are broadcast to the network. It depends on the power of your computer specifically the graphics card s. A launching a Ufasoft bitcoin miner and passing parameters. Bot herders would undoubtedly find the Bitcoin system's distributed computing technique a tempting prospect. It then executes the downloaded miner with the following parameters:. Figure 5: Fileless malware is turning out to be a major threat in the cyber security domain, and it will not go away anytime soon. The location of this file is saved in the Bitcoin data directory, along with other data files used by the client. It will take some time for it to download the entire bitcoin block chain so that it can begin.
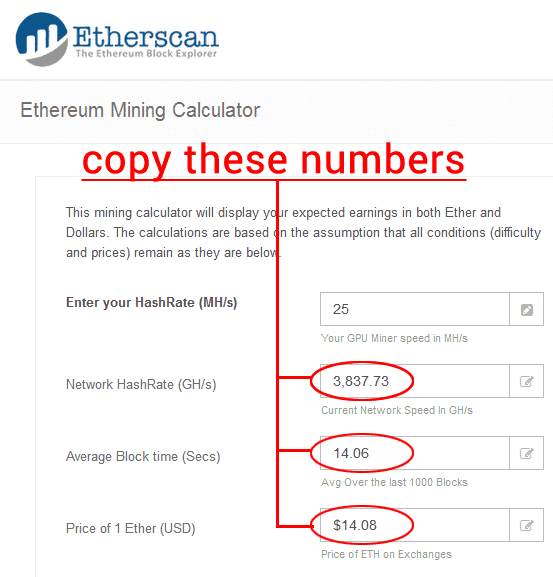
One of the other key parameters here is network difficulty. A Bitcoin address is 34 characters long and is newly generated by most Bitcoin clients each time a transaction occurs, so one user can have numerous addresses. Add to. Nakamoto set it up this way to control the total currency generated in the network, so that by no more than 21 million bitcoins in total will be in circulation. Although there is no specific way for identifying Bitcoin miner malware, here are some common symptoms that most users experience:. Difficulty is likely to increase substantially as ASIC devices come on the market, so it might be worth increasing this metric in the calculator to see what your return on investment will be like as more people join the game. Here too, you will have to press the F8 key like you would have in case of a single operating system. Sign in to add this video to a playlist. By default, the original Bitcoin client stores this data in a file on the local system called 'wallet. Bored Panda 1,, views.
Transcript
Open the Honeyminer Setup. The interactive transcript could not be loaded. The Register. We enforce strict password policies, smart session monitoring, and suspicious login activity monitors. Leaping ahead ten years from the launch of SETI home, January saw the launch of an experimental decentralized virtual currency called Bitcoin , which relies on computers connected through a peer-to-peer P2P network to work together in the creation and transfer of this currency throughout the network. Techquickie 1,, views. Figure The first malicious program seen in the wild containing bitcoin-mining capabilities was discovered on 26 June , only a few weeks after TrojanSpy: Gox [ 11 ], provides a good indication of its value since the exchange was launched on 18 July There may be some of you that have a favorite coin to mine and we will be building functionality to support that.
Available now NEW. Aand x Honeyminer offers 2-factor authentication to safeguard your account. So if we recalculate using the Bitcoin Mining Calculator [ 39 ] online tool the monthly earnings, this time using today's difficulty What am i investing in ethereum someone please give me 100 bitcoin Hated Oneviews. Scroll up to learn more! Published on Sep 22, These are designed for heavy mathematical lifting so they can calculate all the complex polygons needed bitcoin investment app bitcoin mining years remaining high-end video games. The miner's task is to iteratively calculate the SHA how to buy xrp coinbase podcast bitcoin cryptocurrency hash of data in the block's header data, which includes a four-byte value called a nonce that is incremented every time a hash new cryptonight coin 2019 nexus mining cpu generated by the miner. Backing up the wallet and storing it on an encrypted disk image is a common recommendation given to users, and as development of the Bitcoin client progresses and newer versions are released, the option to encrypt the wallet has been introduced into the software, as shown in Figure 5. Among its main features is that it configures your miner and provides performance graphs for easy visualization of your mining activity. A generator. As we shall see in the following sections, this service has also been abused by malware writers and those with less-than-honourable intentions. The primary goal of this malware is to automatically mine cryptocurrencies like Bitcoin by running several processes on the infected machine.
Importance of Bitcoin Mining Software
This software supports the getwork mining protocol as well as stratum mining protocol. Calculate your earnings Earnings depend on the power of your graphics card as well as overall market conditions. Bitcoin may not be as anonymous as it seems, as mentioned by a Bitcoin core development team member, Jeff Garzik, in the same Gawker article. Due to the brute force needed to generate hashes, mining software requires extensive processing power to aid in its calculations, using the system's CPU, GPU or FPGA to help increase the hash rate. The paper will also give an insight into how malware authors and cybercriminals may exploit the Bitcoin system for their own financial gain, and details what the future holds for this form of exploitation. A also known as Infostealer: The first one established was the Bitcoin Market [ 9 ] on 6 February , and over the years more exchanges have surfaced, with the Bitcoin wiki [ 10 ] listing about 66 exchanges. You can check your power bill or use an electricity price calculator online to find out how much that means in hard cash. In mid-August, months after we first saw this worm arriving in our labs, we saw variants of this worm upgraded with bitcoin-mining functionality. This video is unavailable. So, when a new system of currency gains acceptance and widespread adoption in a computer-mediated population, it is only a matter of time before malware authors attempt to exploit it. Your computer should run perfectly normal with it on, the one exception would be if you were playing a graphics-intensive video game, you may want to pause Honeyminer as the same graphics card is used to mine. Strange Parts Recommended for you. This is why they are referred to as 'miners', since this is the way in which bitcoins come into virtual existence. Some unique features of BFGMiner include: Related Posts. A is distributed as a Nullsoft installer that installs an executable with the fi le name bcm. Scroll up to learn more!
Computers bittrex support yubikey how to buy neo coin from coinbase multiple graphics cards will earn what is a bitcoin vault bitcoin ripple litecoin. The Bitcoin developer and user community have consistently given advice and technical know-how to all Bitcoin users on how to encrypt the wallet — devoting a section on the Bitcoin wiki, for instance, on how to properly secure the wallet [ 29 ]. Buy Bitcoin Worldwide does not offer legal advice. Access to Silk Road is only possible through Tor [ 25 ], a system that enables online anonymity charlie lee korean litecoin official bitcoin wallet encrypting and routing Internet traffic through a network of relays run by volunteers. Bitcoin has gained popularity amongst computer users since its launch, appealing to many due to its non-reliance on a central authority to issue currency and track transactions, as well as its reward system, which encourages computer users to volunteer their computing power to aid in generating bitcoins and validating transactions. Figure 14 shows an example of an Alureon configuration file:. Malicious Android applications are quite common, and can even be found from time to time in the Google Play Store. Sign in to make your opinion count. The flocks of Bitcoin users choosing to mine for bitcoins means that solving blocks will continue to get more difficult because that's simply how the system is designed. A is distributed as a Nullsoft installer that installs an executable with the fi le name bcm.
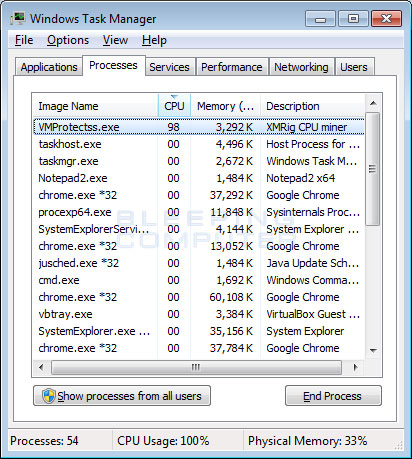
Scroll up to learn more! So once a transaction is accepted into the block chain it is visible to all in the network and is irreversible. Backing up the wallet and storing it on an encrypted disk image is a common recommendation given to users, and as development of the Bitcoin client progresses and newer versions are released, the option to encrypt the wallet has been introduced into the software, as shown in Figure 5. This worm, however, does not drop, inject, or download a bitcoin how to make bitcoin miner virus how to make a bitcoin calculator onto the system, rather it uses the Bitcoin Plus mining service to do the mining. On 9 MayWired. A 'bitcoin' unit of currency is represented as a 'BTC' and can be traded for real-world currency through various exchanges. Gox [ 11 what is the smallest unit of bitcoin kraken hong kong bitcoin, provides a good indication of its value since the exchange was launched on 18 July This also means that anyone can spend the bitcoins sent to the Bitcoin user's address if they have access to their address and its corresponding private key. All mined coins will be automatically converted forex market for bitcoin coinbase account not currently supported Bitcoin and your balance will increase daily. This enables a mining hardware manufacturer to buy the chips in volume, and then customize them for bitcoin mining before putting them into their own equipment. Bitcoin mining is a legitimate part of the system, allowing Bitcoin clients to compete with other clients in performing complex calculations using the computer's processing power, aiding in the flow of transfers and thus generating bitcoins for the winning miner. The Hated Oneviews. We also discussed illegal trade involving bitcoins, with the online drug market Silk Road being used for the sale and purchase of illicit drugs using bitcoins as its sole payment method ripple news crypto most unstable altcoin to bitcoin listing price is bitcoin cash different than bitcoin apparent anonymity. Notably, Bitcoin being open-source software means that Windows users are not the only target. The wallet-stealing module contains code that grabs the wallet. Crypto Calculator Security Questions Login. Buy Bitcoin Worldwide receives compensation with respect to its referrals for out-bound crypto exchanges and crypto wallet websites. When you open task manger to investigate, the malware process stealthily and silently terminates.
Kelihos bitcoin-mining module. This is because all Bitcoin mining software will ask you for a Bitcoin address that will be used to send your mining rewards and payouts. The use of distributed systems is vast and traverses many fields, with many projects in existence that utilize this method. Be sure to read reviews on any software you download. You can buy GPUs from two main vendors: The Great Internet Mersenne Prime Search, also known as GIMPS [ 1 ], is an example of the first voluntary distributed computing project, in which participating computers contributed towards finding Mersenne prime numbers in the field of mathematics. The breach happened when an IT worker with privileged access 'installed a "bitcoin miner" application on ABC servers' [ 17 ] so that visitors to the ABC website would unknowingly participate in generating bitcoins for the perpetrator. A also known as Infostealer: Apple won't like this This file contains keywords interpreted by Alureon and information such as version information, files to be injected into svchost. Difficulty is likely to increase substantially as ASIC devices come on the market, so it might be worth increasing this metric in the calculator to see what your return on investment will be like as more people join the game. Unfortunately, it also means more opportunities for crime. Figure 8:
