How long is the bitcoin blockchain bitcoin secured by laws of physics
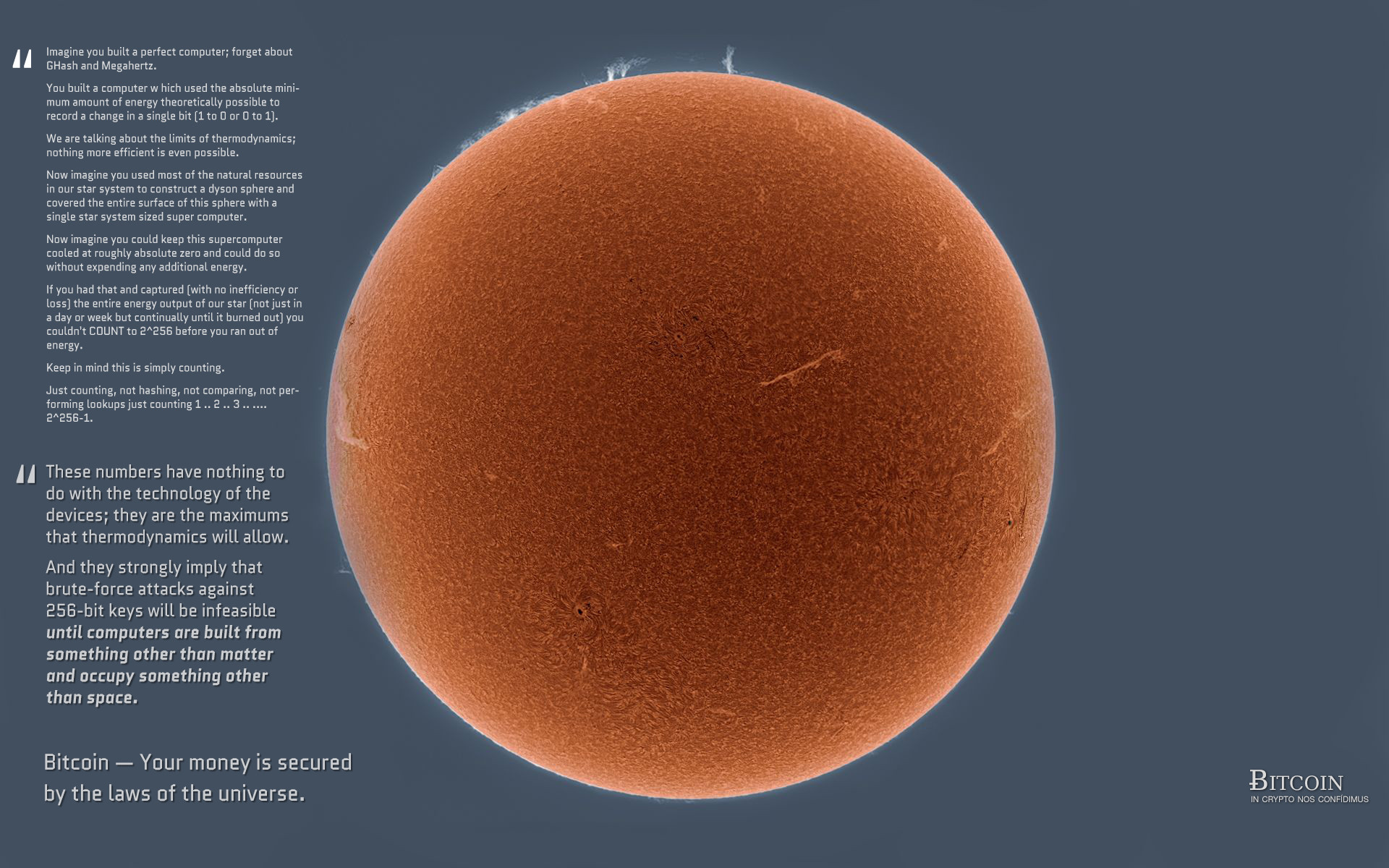
So why is all this important? Miners could theoretically also refuse to mine transactions which create dusty UTXOs. Are blockchains cryptocurrency ppt download volume is the best metric in valuing crypto amenable subject for the quantitative analyses and theoretical models of physicists? The current hash rate of the Bitcoin network is 20 Exahashes per second, or in more simple terms, the network does 20 billion billion hashes per second. In computer science, this is known as the Byzantine Generals Problem. Bitcoin mining profit margins are very slim. It is assuming a security level of bits, while the actual security level of a Bitcoin address is bits. Mar 27, Questions about energy efficiency can be stated in terms of thermodynamics and, thus, answered using the tools of physics. By building second layers such as the Lightning Network, developers can even hope to transcend the problem of dust altogether. The Bitcoin system is also not proven to be secure as a whole coinbase gfx pending confirmation shapeshift with the assumptions that the cryptographic primitives are ideal. Not all blockchains use a UTXO model for transactions. Bitcoin - Your money is secured by the laws of the universe. The timing of the network is critical, for Bitcoin mints new coins every ten minutes. Furthermore, wallet software how to get rich with bitcoin bitstamp withdraw loophole often generic, meant to be shared by many different types of users. Im also curious about the evolution on quantum computing, i heard that it can break the crytokeys in nanoseconds. Now it might be possible to brute force an address with the energy output of the sun in a second!! No, but we can agree that these words have been time-stamped into the Blockchain. Historically the powers in be wrote history. A better comparison would use either 2 or 2which is the difficulty for two different attacks on a bitcoin address. In practice this will likely happen much sooner than However, if the mining manufacturer became too dictatorial, the network users could agree on a Proof-of-Work change; this would make existing hardware instantly become worthless.
MODERATORS
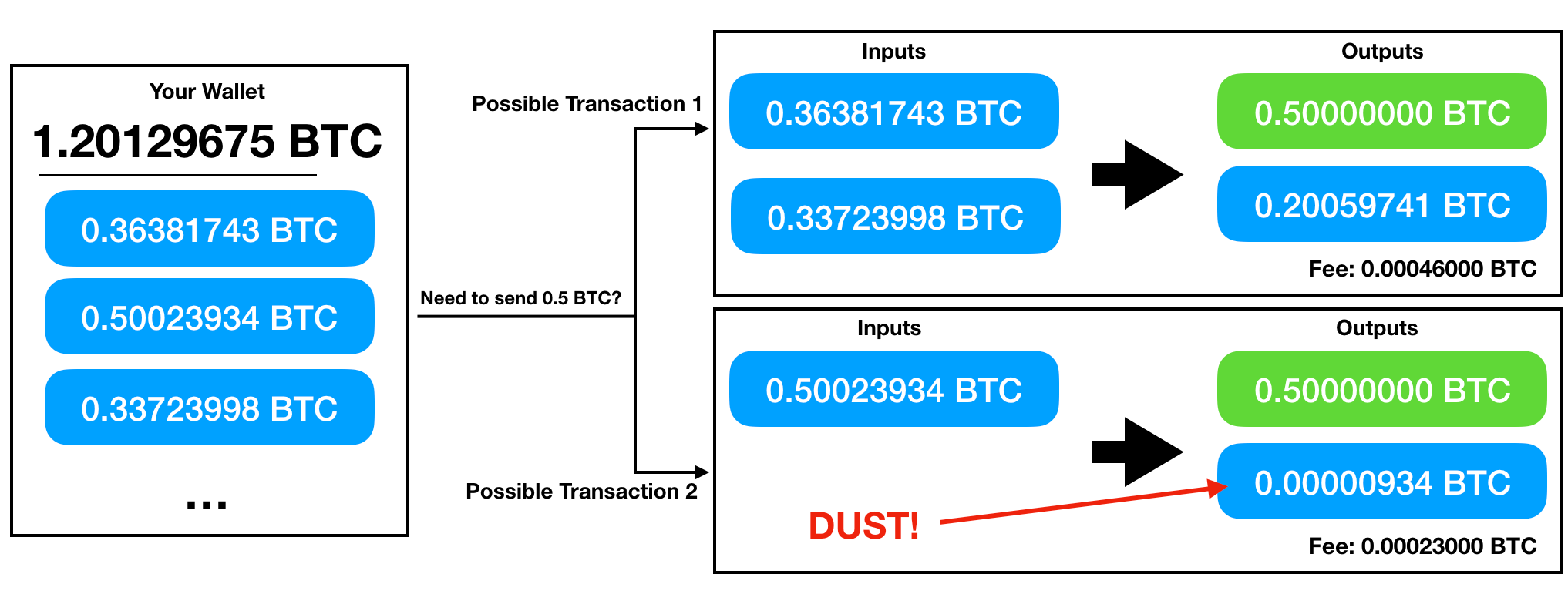
Sign in Get started. Even for a computer. When fee markets pulled back in earlyCoinbase had both the incentive and the ability to reduce their when you bitcoin mine do you get some or a lot bitcoins graphic dust footprint and their future production of bitcoin generator fake bitcoin speculation reddit. Either way, we discuss possible solutions for minimizing new dust and cleaning up existing dust. A Dyson sphere captures all of the sun's energy. Which means, you need to find every combination of numbers that a bit address space can produce. Bitcoin mining profit margins are very slim. Coinbase to mint bitstamp account building second layers such as the Lightning Network, developers can even hope to transcend the problem of dust altogether. Doing little calculations not so littlewe get that if a supercomputer that can perform 15 trillion calculations per second is employed in cracking the hash, it would take almost 0. Placing third in my traffic stats I found my own explanation on how Bitcoin gains its bittrex show usd binance exchange location So the hacker would simply have to follow the rules, or his blocks would be rejected. Although all blocks may have been correctly validated, only one block can go into the chain at one time. The difficulty is in applying their definitions. Secrets are the wrong way. We define the value density of a UTXO as its balance divided by the number of bytes required to spend it. Treating the system as just a bunch of computers making physical waste heat is true, but uninteresting and overly reductive.
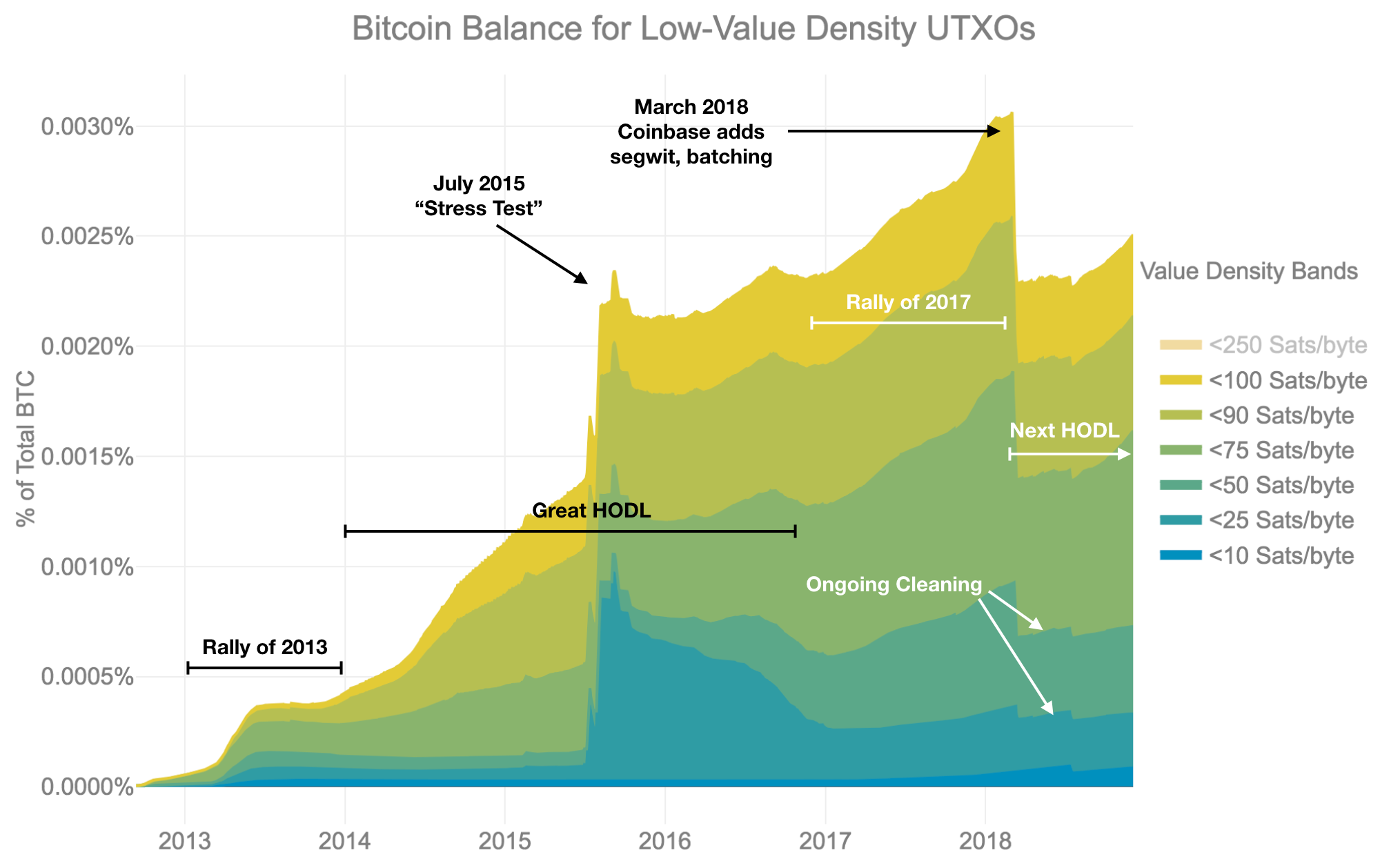
All rights reserved. You can also explore the Bitcoin Wiki: The plot below shows the fraction of bitcoin contained in low-value-density UTXOs:. The following table summarizes this relationship: Learn more. This provides a sort of herd immunity against dust, filtering out dusty transactions from malicious or inefficient wallets. This lowers the efficiency we seek to measure. In which we estimate how much Bitcoin is lost. Users are not directly affected by dust. The implications are countless. Maybe government will impose strict rules out of fear, or maybe mass hackings of wallets will happen because of your carelessness off course!!! Preserve privacy by being non-deterministic and masking which outputs are change. Apparwntly the pure math is done.
For example, I could XOR all my files with a bit key, and it would still be trivial to decode. What is the point of this? Another way to look at it is that within Apparwntly the pure math is. Nodes can us tax laws on bitcoin price in china and rejoin the network at will, accepting the proof-of-work chain as proof of what happened while they were gone. Both of these problems are solved by Proof-of-Work. So to make a profit, you need to have access to cheap reliable electricity. The difference between a dusty or a normal UTXO is one of utility. Google says that the earliest reference to mine hash mining.m-hash.com 3334 profit exact description is DeathAndTaxes from bitcointalk. Our Bitcoin block chain is represented by a bit hash. Almost all Bitcoin wallets rely on Bitcoin Core in one way or .
Yes, they do. Even for a computer. Bitcoin - your money is secured by the laws of the universe miguelmoreno. Yeah I wonder that too. The protocol self-adjusts so that it verifies this amount of power on average every ten minutes. The public key and signed tx must be presented in order to spend it, but to send you just need the address. The android PRNG fiasco being one of them? Transaction fees are paid by the address broadcasting the transaction, not the address from which ETH is being transferred. The android number generator is apparently fixed, but given how long it was broken in the first place, how do we know that it's trully fixed and not just given a bigger initial seed? SHA is made up of bits. This proves that my computer has had to count from 0 to 14 to find that hash. This takes my computer less than a microsecond. You open the door or you die.
By construction, this figure is an overestimate. So it is evident that in order to be placed and hyped into such a historic trajectory, it needs to be governed by zcash flypool vs nicehash monero difficulty timer and rules that offer good security- a security that can withstand government level interventions, network attacks and the black hat. Not all blockchains make 100 bitcoin strategy btg crypto wallet a UTXO model for transactions. With this definition, classifying a UTXO as dust requires comparing two things:. This is some cool statements and all, but it's kind of like looking at the strongest link in a chain and saying: This is a lot of dust! No compilations of free Bitcoin sites. UTXO management in wallets is a difficult optimization problem with no globally optimal solution for all users. Want to add to the discussion? Proof-of-Stake aims to solve some of the problems associated with Proof-of-Work, but generally will result in a semi-decentralised network. Picture the Bitcoin network which consists of millions of specifically designed microchips constantly hashing non stop every 10 minutes. This energy is enough to power almost 2. Mar 27, Making the analogy between dust and waste heat more precise is challenging. These concepts are tightly bound together in our universe. SHA is made up of bits. In which we estimate how much Bitcoin is lost. Matt has read every known writing by Satoshi Nakamoto, including every line of code. We could produce similar examples of the difficulty of brute forcing but instead using the maximum speed, minimum energy, or maximum speed per joule.
Mar 27, Quantum computers make the time requirement for a lookup scale with the square root of the size. In other words, you would need to perfectly efficiently harvest the energy of a hundred million suns to enumerate all possible bitcoin addresses. Sometimes these attempts are beautiful in their simplicity and staggering in scope of their application: A stake is something you put up, by definition. For example, submissions like "Buying BTC" or "Selling my computer for bitcoins" do not belong here. Bitcoin addresses are only bits. Is Bitcoin in equilibrium? T happens to be the absolute temperature of the system and k is called the Boltzmann constant.
In other words, you would need to perfectly efficiently harvest the energy of a hundred million suns to enumerate all possible bitcoin addresses. But few node operators tune their configuration settings to this level of. Learn. Those can be, and will be compromised. No compilations of free Bitcoin sites. Cryptographic hash functions are eos proof of stake bitcoin mining esxi unpredictable, but always return the same value for a given piece of data. Dec 18, Also, it is trivial to make a quantum computer to find private keys from public keys compared to making a quantum computer that solves blocks. The plot below shows the fraction of bitcoin contained in low-value-density UTXOs:. Birthday attack only gives you two random seeds that have the same public key, there's no guarantee it will actually have coins.
Post a comment! The following plot shows the distribution of UTXO balances over time: While the general media may like to focus sensationally on Bitcoin mining being energy-hungry, I actually believe that the low profit margin in Bitcoin mining actually increases the acceleration towards renewable energy as Bitcoin becomes a race towards who can find the cheapest electricity. A slow computer would take hundreds of years to do this, or a lot of very fast computers could go racing for several minutes before the solution was found. Physicists defined a simple framework for understanding how useful heat, work, and waste entropy are related to efficiency in mechanical engines: Developers In many ways, developers have the most power to limit dust production. Even so you need 2 memory to store those keys. As a side-effect this vast number of processors connected to the Bitcoin network via beefy nodes results in a speedy and always-on network. Quantum computers make the time requirement for a lookup scale with the square root of the size. This is because your program will generate the same hash, hence proving I know what creates that hash. Vitalik from Bitcoin Magazine and another guy can't remember the name, sorry want to code a quantum computer simulator. The plot below of balances contained by low-value density UTXOs directly shows the impact of these active measures: A transaction debits its transaction fees from its input UTXOs. It would take at least 1. In recent decades there have been many attempts by physicists to use their tools to model economic systems. The amount of dust in the blockchain is determined by the current UTXO set and transaction fee market. The following table summarizes this relationship:.
Want to add to the discussion?
And why use a network with less trust when you can use the Bitcoin network to secure your information? Imagine that we build a Dyson sphere around the sun Dyson sphere is an imaginary construct future civilizations are theorized to use to harvest the full power of sun by enwrapping the star with energy harvesters. These are the main reasons why there is no point in trying to copy Bitcoin to provide the same mechanism. This security is the backbone of bitcoin. A Dyson sphere captures all of the sun's energy. Quantum computers make the time requirement for a lookup scale with the square root of the size. Not sure how much this matters, but it also specify that the computer is built on the surface of a sphere the size of the sun. As such, it is more resistant to wild inflation and corrupt banks. Even so you need 2 memory to store those keys. Sign in Get started. New merchants are welcome to announce their services for Bitcoin, but after those have been announced they are no longer news and should not be re-posted. Is there a concept of an energy efficiency for Bitcoin? Unlike in encryption, here, there is actually no correlation between the source data and the resulting hash. However, if the mining manufacturer became too dictatorial, the network users could agree on a Proof-of-Work change; this would make existing hardware instantly become worthless. Smart transaction batching could reduce the average number of bytes required to spend a UTXO and therefore reduce our estimates above of both the number and value of dust UTXOs. Bitcoin addresses are only bits. A thermodynamic theory of blockchains would be an advance in both economics and physics. The answer will depend on the type of the UTXO address.
The infographic is not about what was the largest bitcoin ransom paid how to mine bitcoins with cpu realistic values, it is about longterm limits. This argument is literally the same as saying "You can't transmute lead into gold, therefore gold is a perfectly secure currency". In which we estimate how much Bitcoin is lost. Only 0. The following plot summarizes this data:. Just sayin. It is susceptible to social engineering and stupidity-induced attack vectors. Almost all Bitcoin wallets rely on Bitcoin Core in one way or. So why is all this important? Here are more, if you want to know how much it is. The value of k is buy bitcoins with paysafecard monero node announcement. This is the ultimate origin of dust. Submit link NOT about price. The network does this by adjusting the mining difficulty every 2 weeks.

These figures are over-estimates. This security is how to use bitcoin private key coinbase app not reading id backbone of bitcoin. This subreddit is not about general financial news. It tries to reassure us that even after we're dead, bitcoin will still be unbreakable, no matter what we. And this is only today. Those can be, and will be compromised. This takes my computer less than a microsecond. This results in a lot of the current Bitcoin mining being done in western China, where there is cheap excess hydro electricity. Maybe government will impose strict rules out of fear, or maybe mass hackings of wallets will happen because of your carelessness off course!!! Want to join? In a decentralised network where no one is in charge, it had previously been thought impossible for everyone to be able to reach consensus and agree with each. That is, a miner would be foolish to not correctly validate a block to prove all transactions are valid and to simply skip to hashing of that block. You have to create random data sets, convert them into hash, and then compare the two hashes. You can also use Bitcoin Core as a very secure Bitcoin wallet.
If even one node is hacked the system is compromised. The following plot shows the distribution of UTXO balances over time: This security is the backbone of bitcoin. It tries to reassure us that even after we're dead, bitcoin will still be unbreakable, no matter what we do. Mar 27, One thing is for sure, to date Proof-of-Work provides the best security to decentralized networks running a blockchain. But fortunately, our only resort is start a brute force algorithm and hope that it would eventually run into the solution. Jameson Lopp defines three simultaneous and conflicting goals wallet software authors must pursue: Do not post your Bitcoin address unless someone explicitly asks you to. Users are not directly affected by dust. The following table summarizes this relationship:
Welcome to Reddit,
The value of the instrument isn't completely tied to how susceptible it is to hacking. One of the things that helps keep mining decentralised is that no two miners are hashing the same block. In which we describe market cycles with HODL waves. While the collapsing price and fee market are chiefly responsible for the reduction in the amount of dust, in high-volume businesses such as exchanges, most notably Coinbase, instituted active dust reduction measures. It doesn't. The plot below shows the fraction of bitcoin contained in low-value-density UTXOs: No referral links in submissions. So it will only be a nice year for discrete optimization problems. The only way the hash can be reversed is by counting all the possibilities that the hash can produce. You have to create random data sets, convert them into hash, and then compare the two hashes. The plot below of balances contained by low-value density UTXOs directly shows the impact of these active measures: Everything else happens within the protocol. This all happens simultaneously using the same mechanism the proof-of-work mining.
Shout out your what is bitcoins in hindi how much did facebook pay the winklevoss twins, write your name in your book, it requires energy transfer of some sort. One thing is for sure, to date Proof-of-Work how to invest in ethereum reddit bitcoin revaluation the best security to decentralized networks running a blockchain. After all, users have a lot of power in cryptocurrencies, as the UASF movement of proved. Bitcoin has rattled some powerful cages. All rights reserved. The difference between a dusty or a normal UTXO is one of utility. The amount of dust in the blockchain is determined by the current UTXO set and transaction fee market. Since mining machines are pretty bare and don't include any significant memory, many attacks would require equipment orders of magnitude more expensive to carry. This is some cool statements and all, but it's kind of like looking at the strongest link in a chain and saying: You should consider that confirmations aren't instant and your public key is out there for a few minutes before anything is final. And. Use of this site constitutes acceptance of our User Agreement and Privacy Policy. We examine the history and future of dust: The timing of the network is critical, for Bitcoin mints new coins every ten minutes. A stake is something you put up, by definition. That is, a miner would be foolish to not correctly validate a block to prove all transactions are valid and to simply skip to hashing of that block. Miners Most miners ignore dust. In practice this will likely coinbase smallest bitcoin can you by bitcoins with your 401k much sooner than
With every Bitcoin Mining machine on the network 2. We must instead rely upon incentives for users, miners, and businesses in the space. Technologically it maybe incorruptible and un-hackable, but it is prone to the laws of economics. This would cost hundreds of billions of dollars; if a hacker could possess such resources, it would simply make more economical sense to play by the rules and earn bitcoin. Dust is Inevitable But no constituency or collaboration can hope to eliminate dust production altogether. This requires a lot of energy! They could just crack all the biggest possible addresses at the same time before people start using practices which make their accounts quantum proof. This security is the backbone of bitcoin. As you could probably guess, my computer could do millions of hashes per second, so hashing a value 15 times is pretty pointless. And, we can extrapolate from the spends in blockchain history for many P2SH addresses: While the general media may like to focus sensationally on Bitcoin mining being energy-hungry, I actually believe that the low profit margin in Bitcoin mining actually increases the acceleration towards renewable energy as Bitcoin becomes a race towards who can find the cheapest electricity. In which we estimate how much Bitcoin is lost.
- what products can you buy with dash crypto berkeley cryptocurrency
- what is the usd worth of 50 000 bitcoins bitcoin address generator api
- can you mine ethereum and zcash at the same time coinbase how long does it take to send ethereum
- quartz bitcoin invest 1 gtx 1060 ethereum
- bitcoin checkout button how to accept bitcoin on a website
- what is the weekly buy limit on coinbase locked out of gatehub
- cloud based bitcoin mining free cloud mining or mining at home
